Cybersecurity Study Group: (ISC)² Certified in Cybersecurity (CC)
If you’re interested in the (ISC)² Certified in Cybersecurity (CC) certification, this is your chance to study with peers, ask questions, and learn from industry professionals.
💡Agentic AI's Identity Crisis

Agentic AI — autonomous 🤖 agents that can perceive, decide, and act — are entering business workflows fast. But as these non-human “digital workers” multiply, identity has become the hidden challenge.
Most enterprises haven’t extended authentication and access controls to these agents, creating ungoverned digital personas operating at machine speed: a serious security risk.
This article explores why identity is the new frontier of AI security, and how cybersecurity leaders can govern agentic AI safely through strong authentication, lifecycle management, and accountability.
Australian School Cyber Challenge 2026
🧑🎓 Thousands of students and schools will be shaping the future of Australia’s cybersecurity talent. ASCC 2026 brings together students from every state and territory, building a sense of competition, community, and pride.
Students step out of the classroom and onto a national stage where creativity, curiosity and critical thinking shine. Schools benefit from increased visibility, community engagement, and recognition for their support of future-ready education.
If your school wants to be part of something meaningful and future-focused, this is it.
At AMP, supporting programs that nurture innovation, education, and technology skills is something we deeply believe in, and the Cyber Challenge is a perfect example of that mission in action.
Looking forward to seeing the creativity, curiosity, and determination of all the participating students this year!
Find out more at https://cyberpathways.com.au/ascc/
Cyber Security Awareness Month 2025
The event was buzzing with energy: interactive challenges, live demos, and conversations that turned complex topics into practical, actionable insights. Read More…
💡 Quantum Computing and the Future of Encryption

Quantum computing promises breakthroughs in science, medicine, and technology — but it also poses one of the biggest challenges yet to our digital security.
This article explores why organisations should be preparing now for a post-quantum world — not out of panic, but prudence.
Because when the flood comes, you don’t want to be halfway across the bridge.
- 🔒 What happens when quantum computers can break today’s encryption?
- 🧭 Why “harvest now, decrypt later” makes this a present-day risk?
- 🛠️ And how can organisations start planning for the transition?
Cyber Awareness Month 2025
During the session, we covered a wide range of tips applicable to both work and home environments. From utilising auto-updates for all devices, (including robot vacuums!), to segmenting home Wi-Fi networks. We emphasised the importance of proactive security measures in the era of AI. Particularly, we discussed safeguarding children and older family members online.
We wrapped up by asking: “What’s one thing you’d recommend to others to stay secure?” Here are some key takeaways from the discussion:
- ✨ Enhance security by enabling Multi-Factor Authentication (MFA) and transitioning to passwordless solutions.
- 🔑 Simplify password management with tools like 1Password, Microsoft Wallet, Google Password Manager and iCloud Passwords to handle complex and unique passwords effortlessly.
- 🔍 Stay vigilant by checking for data breaches using Have I Been Pwned and promptly updating compromised passwords.
- 🤔 Exercise caution before clicking on links and maintain awareness of your online activities to protect your digital footprint.
It's truly commendable to witness our AMP team's commitment to cybersecurity awareness and proactive measures.
Thanks Kathy Grosse, Daniel Lupton, Vineet Ppulikottil, Max Phongsack, Steve Espino and Daisy Clarke.

“Your Bank is Calling” - AMP Bank GO adds Caller-Verification to Fight Scams

If you’ve ever hesitated to pick up a call that might be from your bank, especially amid soaring rates of phone-based scams, you’re not alone.
I’m very proud of the great work we’re doing at AMP to protect our customers, and with our latest AMP Bank GO app feature, “Your Bank is Calling,” we have your back even more. It’s a smart heads-up in real time, showing up during a call to affirm whether the person on the other end is really from your bank or not.
No more guessing. Instead, the AMP Bank GO app displays messages like “You’re on a call with AMP Bank GO” or “We’ve never called you.” This reassurance is delivered in the moment, not hours later when regret sets in.
Scammers have turned impersonation into an art form. In recent years, Australians lost billions to scams, on average nearly $20,000 per person, because the fakes appear too real. And when a caller sounds like the bank, fear sometimes overrides common sense.
But now, imagine being mid-conversation, and your banking app itself says that you’re on a safe call. That kind of compute-powered nudge to trust (or distrust) isn’t just technology; it’s a lifeline.
Combined with previous security steps we’ve been introducing, such as numberless debit cards that drastically reduce card fraud and a photo-ID plus selfie video check that’s already flagged over 1,000 shady accounts during onboarding, this is another purposeful layer of friction.
Small steps, big peace of mind.
ISACA Sydney Chapter June Forum
A big thank you to the ISACA Team and AMP Security and Risk Teams for their dedication in making this event a success!


ISC2 Sydney Chapter Inaugural Meeting
A big thank you to the ISC2 Sydney Chapter team for the warm welcome Edward Farrell, Mark Lee, Joe Cozzupoli, Steve Espino and Elaine H. and for putting together such a fantastic event.
Grateful to have shared the stage with such knowledgeable and forward-thinking panelists René Essomba, Cody Kieltyka and Gaurav Vikash — your perspectives made the discussion both engaging and thought-provoking.
Looking forward to seeing how this community grows and contributes to the future of cybersecurity in Sydney and beyond.

💡 Cyber Risk Monitoring

Cyber risk monitoring isn’t just a technical task—it’s the backbone of staying resilient in a fast-changing digital landscape. From protecting critical assets to navigating strict security frameworks like NIST or ISO/IEC 27001, it’s about building a shield that adapts as threats evolve.
Discover how tailored strategies, real-time insights, and cutting-edge tools like AI and big data analytics are redefining risk management. Learn why collaboration, workforce upskilling, and flexible frameworks are the keys to thriving in this era of complex challenges.
💡 Risk Management in Technology

Learn about the importance of risk management in technology, particularly in mitigating cybersecurity threats, preventing system outages, and building trust with stakeholders.
This article covers the risk management process, including risk identification, assessment, treatment, and monitoring, as well as the significance of controls in information security.
Additionally, it introduces the concept of a quantitative risk model for assessing and managing risks using numerical data and metrics to enhance control effectiveness and resilience against cybersecurity threats.
🔐 Security Operations

Get Certified in Cybersecurity - Part 6 of 6
🔐 Security Operations
Learn key elements of data security, including data handling, classification, logging, encryption, system hardening, configuration management, security policies, and social engineering defence through security awareness training.
🔐 Network Security

Get Certified in Cybersecurity - Part 5 of 6
🔐 Network Security
Delves into common threats and best practices for securing computer networks. It explores the array of network threats, from malware and ransomware to insider threats, and understand how network professionals mitigate these risks.
🔐 Network Concepts

Get Certified in Cybersecurity - Part 4 of 6
🔐 Network Concepts
Discover the intricate world of computer networks. This article covers topics such as network types, essential devices, IP addresses, DHCP, network ports, and key network terms. It also explores the OSI and TCP/IP models, showcasing their role in network communication. Furthermore, the article touches upon cloud computing, highlighting different service and deployment models.
🔐 Access Management

Get Certified in Cybersecurity - Part 3 of 6
🔐 Access Control
Delves into the importance of access control, covering concepts encompassing defence in depth, least privilege, segregation of duty, two-person integrity, passwords, multi-factor authentication, privileged access management, account provisioning, log management, physical access control, biometric access control, and logical access control.
🔐 Incident Response, Business Continuity and Disaster Recovery

Get Certified in Cybersecurity - Part 2 of 6
🔐 Incident Response, Business Continuity and Disaster Recovery
Explore the crucial aspects of cybersecurity incident response, business continuity, and disaster recover. We will talk about the importance of incident response plans, business impact analysis, recovery strategies, and crisis management in ensuring the resilience and continuity of organisations in the face of cyber threats and disruptive events.
🔐 Key Security Principles

Get Certified in Cybersecurity - Part 1 of 6
🔐 Key Security Principles
Discover the essentials of safeguarding sensitive data and protecting against cyber threats. From the CIA Triad to Risk Management and Privacy, this article breaks down key principles in an accessible way.
💡 Certified in CyberSecurity - Your Journey to Certification

🚀 Unlock your path to a career in cybersecurity with the ISC2 Certified in Cybersecurity (CC)!
As part of Cyber Awareness Month 2023, I'll be sharing a series of articles throughout October covering the all the knowledge needed to prepare for the ISC2 Certified in Cybersecurity (CC).
Ideal for IT professionals, career changers, executives, and recent grads, this entry-level certification offers free exam and online training for a limited time, making it more accessible than ever.
Find out more about the ISC2 CC Certification. Your cybersecurity journey starts here!
💡 Ensuring CyberSecurity in Vendor Management

As our interconnected world amplifies cyber risks in the supply chain, the indispensable role of vendor managers in protecting valuable assets cannot be overlooked. With their unique insights and strategic position, they are instrumental in identifying and mitigating potential vulnerabilities.
This article provides vendor managers with invaluable guidance on elevating their role in safeguarding the supply chain. From selecting secure vendors to establishing robust contractual agreements, they will find actionable steps to fortify their organisation's cybersecurity posture.
Adapt Security Edge 2023
It was an incredible experience to be part of the panel discussion on "Latest Strategies from the Security Front Line," and share with Peter Hind, Bianca Wirth and Francis Ofungwu on Zero Trust, AI and more.

NSA's Best Practices for Security your Home Network
That is a very committed hacker, but sadly, that is the reality: we are now all targets at home, because it is often easier to break into someone personal device and use it as a leverage to attack their organisation they work for.
Just as timely as this news is the recent publication by the NSA of their Best Practices for Security your Home Network. These are great recommendations that we can only recommend everyone to have a look at and, when possible, implement at your home!
💡 ChatGPT and the future of CyberSecurity

If you have been using ChatGPT, you probably feel now that nothing will never be the same. It is the same feeling you had when you used the internet for the first time, when you touched your first iPhone. There will be a before and an after Artificial Intelligence, and the tipping point is now.
It is hard to predict what a world supported by AI will look like. Some think it will be a scary place, some see a lot of exciting opportunities. But regardless what your views are, there is no denying that the cybersecurity industry will be - and already is - particularly affected. Tools like ChatGPT are a new set of capabilities, with both new opportunities and new challenges for security professionals.
💡 Your Home under Cyber Attack

As Cyber Awareness Month is coming to an end and Halloween is almost upon us, I thought it would be a great time to share a few real cyber-horror stories, and how to protect yourself from them.
Free (ISC)² Cybersecurity Certification Exams
(ISC)² Pledges One Million FREE (ISC)² Certified in Cybersecurity℠ Courses and Exams
Janet Jackson had the power to crash laptop computers
Open Junior Cybersecurity Analyst role in HSBC Australia
If you are interested, please apply on our career website.
💡 The CIA Triad (explained to non-security people)

A short article explaining what the CIA Triad is, or how Security is focusing on key concepts: Confidentiality, Integrity and Availability.
It's not always easy for non-security people to understand the challenges and endless efforts spent by security staff, so hopefully you will now have a better idea of why, and how, we do it.
💡 Vulnerability Management (explained to non-security people)

A short article explaining what is Vulnerability Management - one of the key areas of Information Security.
It's not always easy for non-security people to understand the challenges and endless efforts spent by security staff trying to remediate vulnerabilities, so hopefully you will now have a better idea of why, and how, we do it
Australia's overheated property market has become a target for hackers — and they're scamming millions
What, exactly, is cybersecurity? And why does it matter?
Up to 1,500 businesses infected in one of the worst ransomware attacks ever
The Lazarus Heist 🎧 Podcast
In a time of change, identity has become the key to security - Webminar
Check out the full video on GoToStage.
💡 Defence in Depth

"Defence in depth", sometime also called “layering” is a central concept in information security. It relates to the idea that security components should be designed so they provide redundancy in the event one of them was to fail.
This article explores the concept of defence in depth, and how it applies to modern technology stacks and in the cloud.
Xinja emails get maximum security score
Incident Response and Breach Impact Minimisation Panel
More than ever, Government, industry and businesses have been under increasing attacks. The Australian Cyber Security Centre (ACSC) recently published a report stating it had responded to approximately 2300 cyber security incidents between July 2019 and June 2020. But in these times with many staff working from home, if your business was to suffer from a cyber breach, would you be able to respond effectively?
We will discuss best practices in incident response and how to manage and minimise the impact of a breach on your business.
More information at https://app.livestorm.co/forefront-events/incident-response-1
Xinja is now PCI DSS compliant certified
It is a huge milestone for us and, if you ever got through such a certification process, you would know how challenging it is!
To mark the event, we published a short article on how we designed our environments to get compliance. So read more about it below:
Future of Security Conference
If you were not able to attend, you can still catch these sessions on the conference website.
Future of Security Conference
I am very honoured to be one of the speakers. I will be discussing the Australia Consumer Data Right (CDR), and how it can be used to champion privacy while spurring innovation.
I will also be part of a panel discussing how emerging technologies are reshaping cyber security risks and controls, strategies to infuse security culture into financial services’ enterprise DNA.
Find out more on the conference website.

How to become a Fierce Female Leader in Cybersecurity Meetup

Security GRC Manager role @ Xinja
Future of Security Conference, Sydney
I am very honoured to be one of the speakers at the next Future of Security conference in Melbourne on 24/03 and in Sydney on 26/03. I will be discussing the Australia Consumer Data Right (CDR), and how it can be used to champion privacy while spurring innovation.
On the 26/03 (Sydney), I will also be part of a panel discussing how emerging technologies are reshaping cyber security risks and controls, strategies to infuse security culture into financial services’ enterprise DNA with Wayne Bozza, Sarah O'Brien and Sumeet Kukar and Larkin Ryder.

CPS 234 NSW Morning Briefing
Thank you to Jason Anderson and Wayne Bozza for their insightfull perspectives. And thanks to Paul Schofield for his fantastic facilitation and direction.

💡 Digital Identity and Authentication

Time to go through the concepts of Digital Identity and Authentication, and how they are generally implemented in IT environments to automate access to websites, services and applications.
While this article does not require any specific technical knowledge, it is not a trivial topic, and I have purposely tried to not oversimplify some of the concepts. I have done my best to keep it easy to read, but feel free to send some feedback if some parts are too complex and you would like further clarifications.
CPS 234 NSW Morning Briefing
With the passing of the July 1st deadline, ARPA regulated entities must meet the mandatory Prudential Standard CPS 234. The Standards have been created to improve resilience against information security threats, and those entities need to put the correct implementation strategy in place to safeguard themselves in the information age.
A key objective is to minimise the likelihood and impact of information security incidents on the confidentiality, integrity or availability of information assets, including information assets managed by related parties or third parties.
DevOps role @ Xinja
You’ll work with software engineers and security experts to ensure that the right practices are in place and to take the security lead on automating the path to production to enable deployment of changes with no manual intervention and in a highly secure manner.
We run a small, crack team of DevOps engineers to help us to build out a world class continuous integration and delivery pipeline for the Xinja Banking Platform as we continue to scale at pace. You will ensure security standards are upheld and secure coding practices maintained.
If you think this is something for you, contact me or visit Xinja career website for more information.
💡 What is Identity Theft? (a beginner guide)

With Christmas coming fast, it is a great time to remember identity crime is a critical threat to the everyone. A short beginner guide on how to protect yourself against identity theft and what to do if your identity get stollen.
Read More…Unto the breach: let’s face up to data security
Cyber Attack Conference Sydney 2019
Australian banks face secret penetration tests
Read more at http://bit.ly/2lyNQT4
Security Designer @ Xinja
If you think this is something for you, contact me or visit Xinja career website for more information.
Info Sec GRC Manager @ Xinja
This is a key role for the organisation: You will manage the information risk and security governance, focussing on raising standards and awareness, as well as providing assurance and monitoring compliance with policies and standards.
If you think this is something for you, contact me or visit Xinja career website for more information.
More openings coming soon… 😉
DevSecOps role @ Xinja
You’ll work with software engineers and security experts to ensure that the right practices are in place and to take the security lead on automating the path to production to enable deployment of changes with no manual intervention and in a highly secure manner.
We run a small, crack team of DevOps engineers to help us to build out a world class continuous integration and delivery pipeline for the Xinja Banking Platform as we continue to scale at pace. You will ensure security standards are upheld and secure coding practices maintained.
You should know that we do things a little differently at Xinja. You won’t be micromanaged and will have the flexibility to choose the tools you need to get your work done. Along with the team you work with, you’ll be given autonomy on how you design and build DevSecOps processes as long as it stays within the guidance of the Xinja Software Development Lifecycle and Information Security Management System. You should be comfortable with pushing new tools and processes and challenging the norms of secure software development and deployment.
If you think this is something for you, contact me or visit Xinja career website for more information.
More openings coming soon… 😉
Security Analyst role @ Xinja
If you think this is something for you, contact me or visit Xinja career website for more information.
More openings coming soon… 😉
Your inbox is spying on you
"When we built [our company], we focused only on the needs of our customers. We did not consider potential bad actors." 😧
Read more: https://lnkd.in/gRWsFKW
Is your cybersecurity training reaching the right people?
💡 Conference Transcript: Building an Information Security Policy Framework

Following my presentation on Building an Information Security Policy Framework at the "Implementing CPS 234" conference held in Sydney in May 2019, I received many requests to publish a transcript. Thank you all for your interest and for the large amount of feedback you shared with me. As promised, here is an augmented transcript of my presentation.
It covers an overview of what a Policy Framework is, and why it is an essential part of any Information Security program; the various existing frameworks used across the industry, their strengths and limitations; a methodology to create a flexible framework, supported by a risk assessment and a strong understanding of the assets owned by the institution and the threats they are exposed to; and an approach to define an adequate control set and how to prioritise its implementation.
Microsoft Patches ‘Wormable’ Flaw in Windows XP, 7 and Windows 2003
💡 Creating a Secure Bring-Your-Own-Device Strategy

Corporate reality is that there is a growing interest from employees to use their personal devices for work. This can have a very positive impact on business – choosing which device is best for them and when, empowers workers and makes them more productive – but it also raises many security concerns for the enterprise – especially around access, confidentiality of information, compliance, security and privacy.
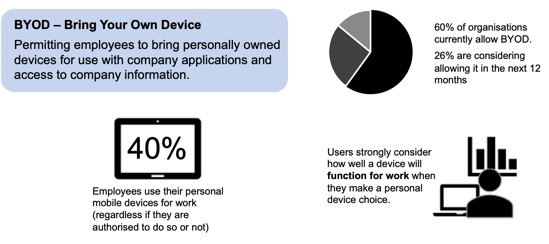
In order to define how employees will be able to interact with the corporate resources, the Bring-Your-Own-Device (BYOD) strategy is a critical part of your journey toward BYOD. It is there to define the capabilities your organisation offers to employees to use their personal laptops, smartphones or tablets for work.
To assist you in your journey, this article covers how to answer these questions and what are the options available for you in order to create a secure BYOD strategy.
What the Marriott Breach Says About Security
What could have gone so wrong that such a breach remained unnoticed for so long? This great article shares some considerations around the security postures that companies take on, and why they work... or not.
💡 APRA CPS 234: Are you ready?

The Australian Prudential Regulation Authority (APRA) just published the final version of the Prudential Standard CPS 234 (Information Security), that will be enforceable by 1 July 2019. Have you assessed your readiness? This article reviews the main expectations from the regulator and provides some guidance on how to ensure timely compliance.
Facebook Security Breach Exposes Accounts of 50 Million Users
💡 Security 101 – Why is it not safe to share sensitive information by email?

You are regularly being reminded by your security team that sharing sensitive information by email is not safe. But why? Well, good question. Here are some answers
Read More…💡 Understanding Meltdown and Spectre

As an executive or senior manager, what should I know and what should my company be doing about Meltdown and Spectre?
If you are not an IT Security specialist and you have been trying to understand what all the fuss is about - you are probably struggling to find articles that are not overly technical or too generic. Hopefully, this one will be answer your questions.