💡 Security 101 – Why is it not safe to share sensitive information by email?
You are regularly being reminded by your security team that sharing sensitive information by email is not safe. But why? Well, good question. Here are some answers
Let's start with a little analogy with the real world. You want to send a bunch of critical hard-copies sensitive documents somewhere to the other side of the city. It's an important delivery and you want to make sure the parcel arrives in time, in good condition, and is not read by someone on the way. What would you do? Let's keep it simple
- ✅ Secure the content: you would securely pack the parcel and seal it, so only the recipient can open it – or at least that you know if someone else than the recipient has opened it.
- ✅ Secure the transport: you would give it to a transport company you trust to deliver it
Let's transpose that to the digital world. So you want to send your bunch of critical documents as soft copies this time. By email of course. What would you do:
- ❌ Secure the content: Unless you, as an individual, have encrypted the content of the email, it will not be encrypted. Your email provider will not encrypt it for. Your security team will not encrypt it for you. NOBODY will encrypt it for you. It is not possible. The content will be plain text. So anybody that will, at any time, be able to access a copy of your email will be able to read its content.
- ❌ Secure the transport: If you are using your company email, you can probably trust them to carry the email security up... the doorstep. The moment the email leaves your company premise, it goes into the hands of number of 3rd parties, some that are contractually obliged to you, and a lot that are not. How do you make sure these parties do not intercept, copy, read or even modify the content of your email? Well, the answer is simple: you can't.
Email content is not secured
Email reality is: anything you write into an email will be sent in a format that everybody can read. Any attachment, except if you have done the effort to encrypt it yourself, will also be fully readable. Why? Because emails were created at a time where security was not a concern.When you send an email to someone, your email server creates a connection to the recipient email server. They exchange data using the Simple Mail Transfer Protocol (SMTP), which is the internet standard for email transmission. SMTP was formally standardised in 1982 and last (minimally) reviewed in 2008 - yep, 10 years ago! It was never designed to ensure the security of the data exchanged.
SMTP is, as its name clearly states, a very simple protocol, and it is one of the reasons it was quickly endorsed and used by everyone. Unfortunately, it is also the reason why it is pretty much impossible to change now. If we were to change the protocol drastically to ensure it is secure, it would really work if every single email server was to use the latest protocol, so they can continue to interact all together. It is hard to say how many email servers there are in the world, but to give you an idea, there were over 1.7 billions websites in 2017. Each website domain name can have 0 or multiple mail servers associated. But if we consider that half of them have a mail server, that over 850 million. That's unlikely to happen anytime soon.
Email transport is not secured
Now that we are clear on the fact that email content is not secure, let's look at the transport. How does the email transit from the sender computer to the recipient computer? And, more importantly, can it be intercepted, read or modified on the way? The diagram below is a (simplified) version of this long journey: 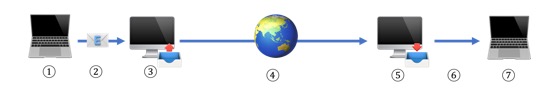
As you can see, there are a few steps between the sender and recipient. The email leaves the sender computer ①, transit into an internal or external network ② to sender email server ③, then transit on the internet ④ to the recipient email server ⑤, and again on an internal or external network ⑥ to finally reach the recipient computer ⑦. If any of these transit points is breached, then the email can be intercepted.
- Let’s put aside the sender computer ① and the recipient computer ⑦. They sure are a risk. Probably the biggest risk, since computer get compromised all the time. But really, that is not something we can blame the email transmission process for. Even if we were able to put in place a super secure process to send emails, as long as users leave post-it with their password attached to their screen, the computer and its content will not be secured.
- Once you pressed “Send”, the email leaves your computer to go ② to your email server. If you are at work, chances are that the email is not leaving your local network and is going straight to the server. Since your company network is probably secure, it is likely to be fine. However, if you are at home or at the café, since get more complicated. The email will go through the local network, to the internet, to you email server. Non-encrypted communication can very easily be intercepted and read by anybody sharing the same network. As you can imagine, when you are using a public WiFi, you have no idea of who else is sharing the network with you, and if they are listening to your communications or not.
- The next stop is your email server ③, managed by your company. It serves as a central point for all emails coming in or out. Of course, you can probably and rightfully expect this server to be secured. However, secured does not mean nobody can read your email. As any application, this server is managed by real persons that have multiple ways to access the email you send and receive. They are probably not supposed to without a good reason, but they can. Keep that in mind.
- The email then leaves the server and travel to your recipient email server via the Internet ④. Part of it will be through your company ISP (Internet Service Provider), which might or might not have a legal obligation to not access the information you are transferring. But the email will very likely also transit via other infrastructures and providers that for sure do not have such obligations. Remember that your email is still travelling non-encrypted, so anybody working for one of these providers can, if they decide to, look at what is going through their pipes, will be able to read without any effort the content of your email.
- The email then arrives at your recipient email server ⑤. While your company might have privacy and security rules to limit your administrators to access your emails (see ③), you have no guaranties that your recipient’s company have the same. If they are using free services like Gmail or Yahoo Mail, it is even the opposite. Terms and Conditions clearly states that these company scan the content of the emails in order to target advertising. So the content of your email will be read at least by a computer, and processed. Do you really want the list of your customers being analysed and stored in some databases for Google to use for advertising? I wouldn’t.
- Similar to ②, the email then transits ⑥ from the recipient email server to the recipient computer. With the same risk
- And finally, the email arrives on your recipient computer ⑦, which we already covered in ①.
Also keep in mind that you cannot recall an email. A lot of solutions (such as Lotus Notes and Microsoft Exchange) claim that – if you use them – you can recall an email sent by mistake. This is only very partially true. It is sometimes possible if both the sender and receiver are using the same technology – which is very unlikely. In reality, for most cases, recalling an email only result in your recipient receiving a courtesy email asking him to delete the email himself. I don’t you know, but when I receive one of those, I become usually very itchy to check what was in that email I am asked to remove without reading.
So as you can see, there are multiple risk points to manage in order simply to send an email from your computer to your recipient computer. Way too many to manage and ensure the communication is secured.
Alternatives
So what can you use instead of email to communicate confidential data to your correspondent? Here are a few simple ideas:- Use a collaboration tool, such as Microsoft Sharepoint, OneDrive, DropBox, Google Drive or more. See what is authorised in your company. These tools are usually well secured, and you can limit the access of your data to selected authorised recipients and even ensure the access automatically disappear after a selected period of time.
- More and more, instant messages platforms (especially professional ones) also have a good level of security. Depending on the nature of the data and the recipient, Skype for Business or Slack could be a good alternative.
- More advance (as they require the installation of an additional infrastructure layer by your IT) are email secure gateways. These solutions basically create a secure layout over the email communication. I have to say I am not a big fan of these solution. They are usually very secure but not very customer friendly, which basically defeat the purpose of using emails altogether.