🔐 Access Management
This article is part 3 (of 6) of a series to help you prepare for the ISC2 Certified in Cybersecurity (CC) certification.
The CC certification is a foundational certification that covers the core concepts and principles of cybersecurity. It is designed for anyone who wants to enter or progress in the cybersecurity field, regardless of their background or experience.
🎓 Become Certified in CyberSecurity series: https://www.jbbres.com/files/cc-2023.html
🎓 ISC2 Certified in Cybersecurity (CC): https://www.isc2.org/Certifications/CC
Information security is a critical concern for individuals and organisations alike. To protect against cyber threats, security professionals use a variety of methods, including physical security measures, logical access control, and access management strategies.
In this article, we will first explore access control concepts, including the three key elements of access control, the principles of defence in depth, and privileged access management. We will then focus on physical security, discussing common examples of physical security measures such as security guards, fences, motion detectors, and more. Finally, we will examine logical access control, covering the different types of technical option to control people access to information and assets.
By implementing a combination of these security measures, individuals and organisations can better protect their sensitive information from unauthorised access and cyber attacks.
Access Control Concepts
Access control is a critical aspect of information security that involves managing who can access particular resources or information within an organisation. This process helps to prevent unauthorised access, misuse, or theft of sensitive data or systems, protecting the confidentiality, integrity, and availability of information.Subjects, Objects and Rules
Access control is based on three essential components, which are subjects, objects, and rules.- Subjects are the individuals or entities that require access to specific resources.
- Objects are the resources themselves that need to be accessed.
- Rules define how and when access should be granted, and they can be based on a variety of factors such as time of day, location, or user credentials.
Defence in depth
Defence in depth, also called layered defence, is a security strategy that involves integrating multiple layers of security controls across an organisation's infrastructure. These layers act as barriers that can help prevent or mitigate the effects of a cyberattack. Defence in depth is designed to make it difficult for attackers to move from one layer to another and to minimise the impact of a successful attack.The strategy integrates people, technology, and operations capabilities to establish variable barriers across multiple layers and missions of the organisation. This means that different types of security measures are deployed in various parts of the organisation's infrastructure, including physical, technical, and administrative controls.
Physical controls include measures such as security guards, locked doors, fences, and alarms.
Technical controls involve the use of technologies such as firewalls, intrusion detection systems, and antivirus software.
Administrative controls are policies and procedures that regulate access to information and resources, including employee training, security awareness programs, and incident response plans.
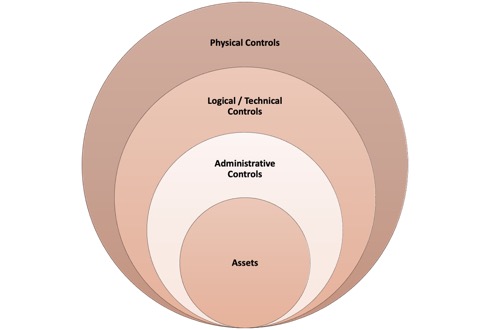
Implementing defence in depth can help organisations minimise the risk of a cyberattack, but it cannot guarantee that an attack will not occur. However, it can increase the likelihood that an attack will be detected early and contained before it causes significant damage. By deploying multiple layers of defence, organisations can create a more resilient and robust security posture.
Least Privilege
Least privilege access is a fundamental principle in access control that revolves around restricting user or system permissions to the minimum necessary for their specific tasks or roles. The idea behind this concept is to limit the potential harm that can result from accidental or malicious actions by users or processes.In practice, least privilege access means that users and processes are granted only the specific permissions and privileges they need to perform their job functions, and no more. This approach helps minimise the attack surface and reduces the risk of unauthorised access, data breaches, and system vulnerabilities.
By adhering to the principle of least privilege, organisations can enhance their overall security posture and better protect their systems and data from potential threats, both from external attackers and insider threats. It's an essential practice in designing and maintaining secure systems and networks.
Segregation of Duty
Segregation of duty (SoD) involves distributing tasks and responsibilities among multiple individuals or departments to prevent any single entity from having excessive or unchecked control over a process or system. The primary goal of SoD is to reduce the risk of fraud, errors, and misuse of privileges by ensuring that critical tasks are divided among different people or entities, thereby creating a system of checks and balances.For example, in a financial organisation, the segregation of duty might be applied to the process of approving and processing financial transactions. One individual may have the authority to initiate a transaction, but another individual, separate from the initiator, must review and approve it. This division of responsibilities ensures that no single person can initiate and approve a potentially fraudulent or unauthorised transaction. By implementing SoD principles, organisations can enhance accountability, prevent conflicts of interest, and reduce the risk of financial misconduct or errors in critical processes.
Two-Person Integrity
The concept of "two-person integrity”, sometimes also called “dual control” is a security practice that requires the presence of at least two authorised individuals to perform critical or sensitive tasks, particularly in environments where trust and security are paramount. This practice adds an extra layer of security by ensuring that no single person can access or manipulate sensitive information or systems without the oversight of another individual. Two-person integrity is often used in scenarios where the consequences of unauthorised actions could be severe, such as in handling classified information, managing financial transactions, or controlling critical infrastructure.For example, in a nuclear launch control facility, two-person integrity would be enforced to prevent any single operator from launching a nuclear weapon unilaterally. To initiate a launch sequence, two authorised personnel, each with a unique set of credentials, must independently verify and authorise the command. This ensures that no one person can initiate such a critical operation without the concurrence of another, reducing the risk of accidental or unauthorised launches and enhancing overall security and accountability. Two-person integrity is an effective safeguard in situations where the potential consequences of a security breach are catastrophic.
Passwords and Multi-Factor Authentication
Passwords are typically a combination of characters, numbers, and symbols that serve as a means of authenticating users and granting them access to systems, applications, and data. However, managing passwords effectively is a multifaceted challenge.One of the key concepts in password management is the need for strong and complex passwords. Strong passwords are difficult for attackers to guess or crack through brute force methods. They usually consist of a mix of upper and lower-case letters, numbers, and special characters. Additionally, it's crucial to avoid using easily guessable information, such as names, birthdays, or common words. To enhance security further, many organisations implement password policies that enforce regular password changes and set minimum complexity requirements.
Accounts and passwords must be unique for each individual and not be shared in order to remain effective. Sharing passwords increases the risk of unauthorised access to your accounts. This can lead to data breaches, identity theft, and compromised online security. In addition, sharing passwords makes it difficult to trace any unauthorised actions or changes to an account back to a specific individual. In cases of wrongdoing or security breaches, it becomes challenging to determine who was responsible, which can hinder investigations and accountability.
Another crucial concept is Multi-Factor Authentication (MFA), sometime also referred as Two-Factor Authentication (2FA). MFA enhances security by requiring users to provide two or more forms of authentication before granting access. Typically, this involves something the user knows (a password). something the user has (a temporary code from a smartphone app or a physical token) and/or something the user is (a biometric, such as fingerprint or facial recognition).
MFA significantly reduces the risk of unauthorised access, even if an attacker manages to obtain a user's password. This additional layer of security is particularly important for protecting sensitive accounts, such as email, online banking, and cloud services, and has become a standard practice in modern cybersecurity.
Privileged Access Management
Privileged Access Management (PAM) is a security practice that helps organisations manage and control privileged access to critical systems and sensitive data.Privileged access refers to administrative access or control over a system, application, or data that can be used to make significant changes, such as adding or removing users, changing system configurations, or accessing sensitive data.
For example, an IT administrator may need admin privileges to install software or update systems. However, when they are performing routine tasks, they do not need admin privileges. Privileged Access Management ensures that admin privileges are only granted when needed and limits the risk of accidental or intentional misuse of admin privileges.
PAM reduces the risk of data breaches and cyberattacks by controlling and monitoring privileged access. It does this by allowing admin privileges to be used only when needed. This means that users are given temporary administrative access only for specific tasks or periods of time. In addition, more stringent controls such as multi factor authentication , increased logging and increased auditing are associated with admin accesses. This reduces the risk of an attacker gaining access to sensitive data or systems through a compromised admin account.
To implement PAM, organisations must first identify which systems and data require privileged access controls. Then, they must define and implement policies for privileged access management. This includes controlling the creation, modification, and deletion of admin accounts, monitoring privileged access activity, and conducting regular audits of privileged access.
Overall, PAM is an essential practice in ensuring the security and integrity of an organisation's critical systems and data. By managing and controlling privileged access, organisations can reduce the risk of data breaches and cyberattacks.
Account Provisioning
User provisioning is a critical process in the management of access controls, ensuring that employees and other authorised individuals are granted appropriate levels of access to information systems and applications.The process of user provisioning typically involves creating new user accounts, modifying existing accounts, disabling or deleting accounts when necessary, and managing access rights based on job roles or other criteria. User provisioning helps organisations maintain control over who has access to sensitive data, applications, and other resources.
- When a new employee joins an organisation, an account must be created for them. This process is commonly known as “on-boarding." During the on-boarding process, IT administrators create a new account for the employee, assign them a unique username and password, and grant them access to the systems and applications necessary to perform their job.
- In the event of a change in an employee's job responsibilities, their account may need to be modified. For example, if an employee is promoted to a managerial role, they may require access to additional applications or systems. Alternatively, if an employee is transferred to a different department, their access to certain systems may need to be revoked or modified.
- Temporary leave of absence or a termination of employment may also require account modifications. Accounts can be temporarily disabled during a leave of absence, and later reactivated when the employee returns to work. When an employee leaves the company, their account should be deleted or disabled to prevent any unauthorised access to sensitive data.
- The process of deleting or disabling an employee's account is known as "off-boarding." During the off-boarding process, IT administrators revoke the employee's access to systems, applications, and data. They may also back up or transfer any important data that the employee created during their tenure with the organisation. Proper off-boarding procedures are crucial to maintaining information security and protecting the organisation's assets.
Log Management
In the context of access control, effective log management takes centre stage as it plays a pivotal role in safeguarding critical systems and data. The management of access logs involves the meticulous gathering of data, detailing the connections of individuals to various systems and their activities within. This invaluable resource not only serves as a historical record but also acts as a vigilant guardian, aiding in the early detection of anomalies.Access logs document each connection, disconnection and activity. They record the journey of every user as they navigate through systems, applications, and data. These logs can capture a large set of data user identities, timestamps, locations, and the actions taken, creating a comprehensive record of access events.
Through logs, security teams can gain the ability to discern the extraordinary from the ordinary, identifying peculiarities that might raise a red flag. Anomaly detection algorithms, sometimes powered by artificial intelligence and machine learning, sift through these logs, searching for deviations from the established norms.
One of the key anomalies that log management can uncover is the phenomenon of "impossible travels." This is when a user's activity suggests that they have accessed a system from two distant or conflicting locations in a very short timeframe, which would not be humanly impossible. For instance, if a user logs in from New York and, mere minutes later, attempts to log in from Sydney, such an event would be flagged as an anomaly, as it defies the laws of physics.
Furthermore, log management systems are designed to identify and report unusual connections. They scrutinise the origin of connections – pinpointing whether it's a new device, an unfamiliar IP address, or a device type that doesn't conform to the usual patterns. When an anomaly is detected, the system can trigger alerts or even automatically take action to limit or prevent potential threats.
In essence, log management transforms access logs from passive records into active guardians of security. By tirelessly monitoring and scrutinising each user's journey, these logs play a pivotal role in information security, making it significantly more challenging for unauthorised access and potentially thwarting cyber threats before they can cause substantial harm.
Physical Access Control
Physical security is a crucial aspect of information security that involves protecting the physical assets of an organisation, such as its buildings, data centres, and other facilities. Physical access controls are designed to prevent unauthorised individuals from physically accessing these assets. These controls can range from basic measures, such as locks and keys, to more sophisticated systems that use advanced technologies like biometrics.There are various physical access controls that can be implemented to protect an organisation's assets. Some common examples include:
- Security guards: Trained personnel who monitor and control access to a facility or area.
- Fences: Physical barriers that prevent or restrict access to a specific area.
- Motion detectors: Sensors that detect movement and alert security personnel of unauthorised access.
- Locked doors/gates: Physical barriers that require a key, code, or other credential to open.
- Sealed windows: Windows that are sealed or reinforced to prevent break-ins.
- Lights: Lighting systems that can deter intruders and enhance visibility.
- Cable protection: Measures to secure and protect network cables, such as cable locks or conduit.
- Laptop locks: Physical locks that secure laptops to desks or other objects.
- Badges: Identification cards that are required for access to a facility or area.
- Swipe cards: Magnetic or proximity cards that are used to access a facility or area.
- Guard dogs: Trained dogs that can detect and deter intruders.
- Cameras: Video surveillance systems that can monitor and record activity in a facility or area.
- Mantraps/turnstiles: Physical barriers that allow only one person to pass through at a time, usually used in high-security areas.
- Alarms: Audible or silent alarms that alert security personnel of unauthorised access or other security breaches.
Biometric Access Control
Biometric access control is a sophisticated security technology that leverages unique physiological or behavioural characteristics of individuals to grant or deny access to physical or digital spaces. This approach offers a high level of security and convenience because it relies on traits that are difficult to replicate or steal, making it a popular choice for enhancing security in various applications.One common example of biometric access control is fingerprint recognition. Each person's fingerprint is unique, and modern systems use advanced algorithms to scan and compare the ridges and patterns on a person's fingertip to a stored database of authorised users. When the presented fingerprint matches an authorised record, access is granted. This technology is widely used in smartphones, laptops, and secure building entrances.
Another example is facial recognition, which identifies individuals by analysing distinct facial features like the distance between the eyes, the shape of the nose, and the contours of the face. Facial recognition is employed for unlocking smartphones, as well as in surveillance and airport security systems.
Voice recognition is yet another biometric access control method, relying on the unique vocal characteristics of an individual, such as pitch, tone, and speech patterns. Voice recognition systems are used in some call centres and to provide secure access to certain software applications.
These biometric technologies offer a level of security that surpasses traditional methods like passwords or keycards since they are based on characteristics that are incredibly difficult to forge or replicate. However, they also raise concerns about privacy and data protection, so their deployment is often subject to stringent regulations and guidelines to ensure individuals' rights are safeguarded.
Logical Access Control
Logical access control is the process of controlling access to computer systems, applications, or data using various methods such as authentication, authorisation, and accounting. It involves the use of software-based mechanisms to manage access to resources and data.There are three main types of logical access control:
- Discretionary Access Control (DAC): This is a type of access control where the owner of a resource decides who is authorised to access that resource. The owner can also grant permission to other users to share the resource with other individuals. In DAC, the access control decision is made by the user, rather than the system. For example, in a shared folder on a computer, the owner can grant permission to other users to read or edit files within the folder.
- Mandatory Access Control (MAC): This is a type of access control where access is determined by the security clearance level of the user and the security classification level of the resource. In MAC, access decisions are made by the system, rather than the user. This type of access control is often used in military or government environments. For example, a document that is classified as "top secret" can only be accessed by users who have the appropriate security clearance.
- Role-Based Access Control (RBAC): This is a type of access control where access is determined based on the user's role in the organisation. Users are assigned to specific roles, and access to resources is granted based on the role assigned to the user. For example, a human resources manager may have access to sensitive employee information, while a regular employee may only have access to their own information.
Most software applications and systems have graphical user interfaces (GUI) that allow users to manage various settings and configurations. These configurations can include access controls, such as user permissions, network settings, or encryption settings. For example, a system administrator may use a software GUI to configure user permissions on a server. The administrator can grant or revoke access to specific resources, applications, or files based on a user's role or job responsibilities.
Another way to manage logical access control is through hardware settings done with switches, jumper plugs, or other means: for example, a computer might have a physical switch that disables USB ports or other external devices to prevent unauthorised data transfer. Another example is a network switch that can be configured to block certain ports or devices from accessing the network. These types of access controls are typically used by system administrators and technicians to prevent unauthorised access or to troubleshoot hardware issues.
Overall, logical access controls play a critical role in protecting sensitive information and resources by ensuring that only authorised users or systems have access. The type of access control used will depend on the specific needs and requirements of the organisation.
Conclusion
In conclusion, a comprehensive approach to information security involves implementing measures to address physical and logical access controls.Physical security measures involve protecting the physical environment and assets of an organisation through a range of tools and techniques, such as security guards, fences, motion detectors, and surveillance cameras. Logical access controls, on the other hand, involve implementing measures to control access to digital resources and data, such as through role-based access control (RBAC), mandatory access control (MAC), and discretionary access control (DAC).
Access controls are an essential component of an organisation's information security strategy, helping to ensure that only authorised personnel have access to critical systems and data. In addition, the use of comprehensive logging and monitoring practices can help to detect and respond to security incidents and breaches. By implementing a combination of physical, logical, and access controls, organisations can help to reduce their overall risk and enhance the protection of their critical assets and resources.
https://forms.office.com/r/EbR6GWvQZcCheck your readiness with a Quiz:
Disclamer: This article is not legal or regulatory advice. You should seek independent advice on your legal and regulatory obligations. The views and opinions expressed in this article are solely those of the author. These views and opinions do not necessarily represent those of HSBC or its staff. Artificial Intelligence Technology was used to read-proof this article.