🔐 Network Security
This article is part 5 (of 6) of a series to help you prepare for the ISC2 Certified in Cybersecurity (CC) certification.
The CC certification is a foundational certification that covers the core concepts and principles of cybersecurity. It is designed for anyone who wants to enter or progress in the cybersecurity field, regardless of their background or experience.
🎓 Become Certified in CyberSecurity series: https://www.jbbres.com/files/cc-2023.html
🎓 ISC2 Certified in Cybersecurity (CC): https://www.isc2.org/Certifications/CC
Network security stands as a bulwark against the ever-evolving array of threats that can compromise the integrity, confidentiality, and availability of sensitive data. The realm of network security is a dynamic and complex one, marked by a constant battle between defenders and adversaries. In this article, we delve into the world of network security, aiming to demystify the terminology and shed light on the common threats and best practices for securing computer networks.
From the insidious spread of malware and ransomware to the sophisticated tactics of hackers and the dangers posed by insiders, network security encompasses a wide range of challenges. Understanding these threats is the first step towards developing effective countermeasures.
To identify and mitigate these threats, network professionals employ a variety of tools and strategies, including Intrusion Detection Systems (IDS), firewalls, and Network Access Control (NAC). We'll explore how these tools work together to safeguard network environments.
Additionally, network security isn't just about digital defences; it extends to physical security measures, such as those in data centres, to ensure the uninterrupted operation of critical systems.
In the following sections, we'll break down the essential components of network security, ranging from secure network design principles like network segmentation and Zero Trust to secure Wi-Fi practices and the protection of data centres.
By the end of this article, you'll have a comprehensive understanding of network security and the knowledge needed to fortify your digital assets against the ever-present threat landscape.
Network Threats and Attacks
Network attacks are malicious actions aimed at disrupting or compromising the security of computer networks and the data they contain. These attacks can be carried out by individuals with malicious intent, hackers, or even insiders with access to the network. Let's explore some common types of attacks and understand them in non-technical terms:- Malware (Malicious Software): Malware is a broad term encompassing any software designed with malicious intent. It includes viruses, worms, Trojans, ransomware, adware, and spyware. Malware can damage systems, steal information, or grant unauthorised access to devices.
- Virus: A computer virus is a type of malware that attaches itself to legitimate programs or files. It has the ability to replicate and spread to other programs, files, or devices. When activated, viruses can cause harm by corrupting files, disrupting system functions, or slowing down the infected computer.
- Worm: Similar to a virus, a worm is a standalone malware program. What sets it apart is its capability to self-replicate and spread across networks without the need to attach to other files or programs. Worms can consume network bandwidth and cause disruptions on a large scale.
- Trojan: A Trojan is a deceptive malware program that disguises itself as harmless or legitimate software to trick users into installing it. Once installed, it opens a backdoor, allowing hackers to gain unauthorised access to the victim's device or steal sensitive information without the user's knowledge.
- Ransomware: Ransomware is a malicious software that encrypts a victim's files or entire system, rendering them inaccessible. Attackers then demand a ransom, typically in cryptocurrency, in exchange for a decryption key to unlock the files. Paying the ransom is discouraged as it may not guarantee data recovery and can incentivise further criminal activities.
- Adware/Spyware: Adware displays unwanted advertisements to users, while spyware secretly collects personal information without consent. Both types of malware can negatively impact system performance and user privacy.
- Rootkit: A rootkit is a stealthy malware that hides its presence from security software and allows unauthorised access to a computer or network. It often acts as a backdoor, enabling other malicious activities to occur undetected.
- Network reconnaissance: Network reconnaissance, also known as information gathering or footprinting, is the initial phase of a cyberattack or a critical step in cybersecurity assessments. During this phase, individuals or organisations attempt to gather information about a target network to understand its structure, vulnerabilities, and potential points of entry. Network reconnaissance is a necessary step for both legitimate network administration and security assessments, as well as for malicious activities such as hacking. Examples of techniques used for network reconnaissance are:
- Port scanning: Port scanning is used to discover open ports on a target system. It involves sending requests to a range of network ports to determine which services or applications are actively listening and accessible on the target. By analysing the responses or lack thereof, attackers or administrators can assess the network's configuration, identify potential vulnerabilities, and understand the services available on the target system, aiding in security assessments and potential exploitation or protection efforts.
- Ping Sweep: A ping sweep is a network scanning method in which a series of "ping" requests are sent to a range of IP addresses. “Ping” requests are short messages sent to systems to check if they are active. When receiving a “ping” request, the system respond with a similar short answer to inform it is active and receiving the request. The goal is to identify active hosts within that range by observing which IP addresses respond to the ping requests. Ping sweeps are often used by network administrators for network inventory and security assessment purposes.
- DoS/DDoS (Denial of Service / Distributed Denial of Service): In a Denial of Service (DoS) attack, an attacker overwhelms a network or website with a high volume of fake requests, causing it to slow down or become unavailable. Distributed Denial of Service (DDoS) attacks involve multiple devices working in unison to amplify the attack's impact.
- Fragment Attack: Fragment attacks involve sending network packets in an abnormal and confusing manner, making it challenging for the network to correctly reassemble them. This can lead to errors and disrupt communication between devices.
- Oversized Packet Attack: In an oversized packet attack, the attacker sends packets that are too large for the network to handle efficiently. This can cause network congestion, degrade performance, and potentially lead to system crashes.
- Ping Flood Attack: In a ping flood attack, the attacker overwhelms a target system with an excessive number “ping” requests. This flood of requests can consume the target's resources and disrupt its normal operations, leading to network congestion or unresponsiveness.
- Tear Drop Attack: The "Tear Drop" attack is a form of DoS attack that disrupts systems by sending intentionally overlapping and malformed fragmented packets. This exploit targets how systems reassemble these packets, causing crashes or unresponsiveness.
- Spoofing: Spoofing attacks involve the attacker impersonating someone else by falsifying their identity. For example, they may forge the source address of network packets to make it appear as if the data is coming from a trusted source, which can lead to unauthorised access or data manipulation.
- Man-in-the-Middle (MITM) or On-Path: In a MITM attack (sometime referred as an On-Path attack), the attacker intercepts and relays communications between two parties without their knowledge. This allows the attacker to eavesdrop on sensitive information or modify data before passing it on to the intended recipient.
- Network sniffing, often conducted with the aid of a device called a network tap, involves the interception and examination of data packets as they travel across a network. This technique is employed for various purposes, including troubleshooting network issues, monitoring for security threats, and analysing network performance, but can also be used for MITM attacks. Network taps operate by duplicating data transmissions from the network and sending them to a monitoring device or software tool for analysis, without affecting the original network flow.
- Code/SQL Injection: Code or SQL injection attacks exploit vulnerabilities in websites or applications to insert malicious code. This can lead to unauthorised access, data theft, or manipulation of the targeted system.
- XSS (Cross-Site Scripting): XSS attacks involve injecting malicious scripts into web pages viewed by other users. When these compromised pages are visited, the scripts execute and can steal sensitive information or perform unauthorised actions on behalf of the user.
- Buffer Overflow: A buffer overflow is a software vulnerability that occurs when an application or program doesn't properly handle data input. Attackers exploit this weakness by sending more data than a program's buffer can handle, causing the excess data to overflow into adjacent memory locations. This can lead to the execution of malicious code, system crashes, or unauthorised access to the affected system.
- Privilege Escalation: Privilege escalation attacks occur when an attacker gains unauthorised access to a system or network and elevates their user privileges, often allowing them to access sensitive information or perform actions typically reserved for administrators.
- Side-channel Attack: Side-channel attacks focus on exploiting information inadvertently leaked during normal system operations, such as power consumption patterns or electromagnetic emissions. These attacks can provide insights into sensitive data or cryptographic keys.
- Insider Threat: An insider threat involves individuals with authorised access to a network, such as employees or contractors, using their position to commit malicious acts, such as stealing sensitive data, sabotaging systems, or causing harm to the organisation from within.
- Logic Bomb: A logic bomb is a type of malicious code that is intentionally inserted into a system or software to execute a particular set of actions when specific conditions are met. Unlike viruses or malware that spread, a logic bomb remains dormant until triggered by predefined criteria, such as a particular date, a specific user's action, or even the removal of an individual's access rights. Once activated, it can execute a range of destructive actions, from corrupting data to causing system failures or initiating other forms of cyberattacks. This form of cyber threat is often covertly planted by insiders or individuals with authorised access to the system and are activated by specific events, for example if the individual leaves the organisation.
Identifying and Mitigating Network ThreatsIdentifying ThreatsThe first step in network security is identifying potential threats. Here are some tools used by security professionals to help in this process:
- Intrusion Detection System (IDS): An IDS is a system that monitors systems and networks for any suspicious activities or patterns that might indicate an intrusion or unauthorised access. When it spots potential threats, it generates alerts, allowing network administrators and security analysts to take appropriate action.
- Network Intrusion Detection System (NIDS): A NIDS is a specialised type of IDS that focuses on monitoring network traffic for any signs of intrusion or suspicious behaviour. It is strategically placed at key points in a network to analyse traffic as it flows through, providing a comprehensive view of network activity.
- Host Intrusion Detection System (HIDS): A HIDS monitors the activities and events on individual host computers or devices. It looks for signs of intrusion, malware, or abnormal behaviour on the host, providing a more focused approach to threat detection.
- Security Information and Event Management (SIEM): SIEM systems collect and analyse log data and security events from various sources across a network. They provide a centralised platform for detecting and responding to security incidents, making it easier to manage network security.
Preventing Threats
Once threats have been identified, the next step is to prevent them. Here are some solutions commonly used for threat prevention:
- Antivirus Software: An antivirus software is designed to detect, quarantine, and remove malicious software (viruses, malware, etc.) from devices. It scans files and processes in real-time to identify and block threats, providing a basic level of protection for your network.
- System and Vulnerability Scans: Regular system and vulnerability scans help identify and patch security vulnerabilities before attackers can exploit them. These scans are like routine health check-ups for your network, ensuring it remains secure.
- Firewalls: Firewalls filter incoming and outgoing traffic based on predefined rules. They act as a barrier between a trusted internal network and untrusted external networks, blocking unauthorised access and preventing malicious traffic from entering the network.
- Intrusion Prevention System (IPS): An IPS not only detects but also actively blocks and prevents potential threats in real-time. It can automatically respond to known threats based on predefined rules, providing an additional layer of security. Specialised IPS, such as Network Intrusion Prevention System (NIPS) and Host Intrusion Prevention System (HIPS) can also be used to ensure more granular protection.
- Data Loss Prevention (DLP): DLP solutions employ a combination of technology and policies to detect, monitor, and protect sensitive information from unauthorised access, sharing, or theft. It works by recognising patterns of sensitive data (such as name, phone numbers, passwords or passport numbers) and apply rules to alert or block the data extraction or transmission.
- Patching: Patching operating systems, applications, and network devices is of paramount importance in cybersecurity. Regular updates provide essential fixes and enhancements to software and hardware, closing vulnerabilities that could be exploited by cybercriminals. By applying patches promptly, organisations bolster their defences against a wide array of threats, from malware and ransomware to data breaches and network intrusions. Failure to keep systems up-to-date can leave them susceptible to known security flaws, effectively leaving the digital doors open to attackers. Patching acts as a proactive measure, akin to fortifying a building against potential break-ins by shoring up weak points in its structure.
Threat detection and prevention are critical aspects of network security. Various tools and strategies are employed to identify and mitigate threats, and the responsibility for these measures varies depending on the cloud service and deployment model being used.
Secure Network Design
A key aspect of protecting a network is ensuring that it is designed secured. While detection and threat prevention are essentials, planning a robust network designed to reduced attack points and limit impact when under pressure is a crucial part of an IT infrastructure.
But creating a secure network is a complex task that requires careful planning, strategic design, and multiple layers of defence.
Network Segmentation
Network segmentation is a fundamental strategy for bolstering the security of computer networks. It involves dividing a large network into smaller, isolated segments or subnetworks. The primary goal is to compartmentalise network resources, control access, and minimise the impact of security breaches. Two common approaches to network segmentation are micro-segmentation and the use of a Demilitarised Zone (DMZ).
Micro-segmentation
Micro-segmentation is the process of breaking down your network into smaller, more manageable parts. Each segment has its own security measures, limiting access to authorised personnel only.
Each segment is fortified with its own set of security measures, acting as a unique layer of defence. It means that even if one segment is compromised, the rest of the network remains safe.
Access to each segment is restricted to authorised personnel only. This ensures that sensitive data is accessible only to those who need it.
Demilitarised Zone (DMZ)
The Demilitarised Zone (DMZ) is a subnetwork that contains and exposes an organisation’s external-facing services to an untrusted network, typically the Internet. that serves as a buffer or intermediary zone between an organisation's internal network and the Internet, adding an additional layer of security to an organisation’s local area network (LAN).
External-facing services, such as web servers, email servers, or application gateways, are placed in the DMZ. These services need to interact with the outside world, and the DMZ provides a controlled environment for this interaction.
Secure Ports vs. Unsecure Ports
Network ports are logical constructs that identify specific processes or services running on a host. Secure ports are those that are carefully monitored and only allow authorised traffic to enter. Unsecured ports, on the other hand, are potential weak points that may be exploited by attackers. A number of network solutions implemented in the early ages of computing did not include security. It’s important to manage these ports carefully to ensure network security and use adequate secure alternatives when available.
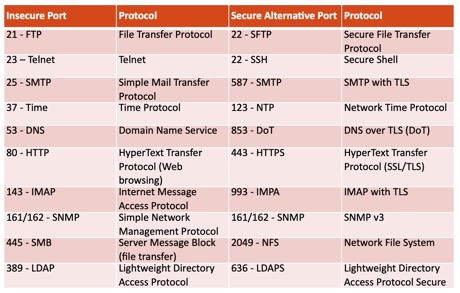
Virtual Local Area Network (VLAN)
A Virtual Local Area Network (VLAN) is a networking approach that allows organisation to group devices together logically, as if they were on separate physical networks, even when they are physically connected to the same network infrastructure. VLANs create isolated segments within a network, providing several benefits:
- Segmentation: VLANs divide a single physical network into multiple virtual networks. This segmentation helps in organising and managing network traffic more efficiently.
- Enhanced Security: By separating devices into different VLANs, organisations can restrict communication between them. This isolation prevents unauthorised access and enhances security.
- Traffic Control: VLANs enable organisations to control and prioritise network traffic based on the needs of each virtual network. This ensures that critical data gets priority and doesn't compete with less important traffic.
Virtual Private Network (VPN)
At its core, a Virtual Private Network (VPN) is a secure tunnel carrying the internet traffic, protecting the data it transport from prying eyes and potential threats.VPNs work by establishing an encrypted connection between two devices or networks. This encrypted connection is often referred to as a "tunnel."
For example, if a user connect to the Internet or an organisation network through a VPN, their data packets destined to the organisation network are routed through this secure tunnel. As data travels through this encrypted pathway, it becomes indecipherable to potential snoopers, including hackers, internet service providers (ISPs), or government agencies. The VPN server, situated in a chosen location (usually the organisation data centre), acts as a middleman between the user's device and the broader internet or corporate network. In essence, it's like sending your data through a secret, secure conduit, ensuring privacy and security in an otherwise public and potentially insecure digital environment.
VPNs serve several vital functions:
- Remote Access: VPNs enable employees to connect to the company's network remotely. This is invaluable for today's increasingly mobile and remote workforce. It creates a secure tunnel that extends from an employee's device to the corporate network, ensuring that sensitive data remains protected during transit.
- Data Encryption: Through a VPN, data is encrypted. This encryption prevents unauthorised access and ensures that even if data packets are intercepted, they remain unintelligible to prying eyes.
- Access Control: VPNs enforce strict access controls, ensuring that only authorised personnel can connect to the corporate network. Employees must authenticate themselves before gaining entry, adding an essential layer of security.
- Protection on Public Networks: When connecting to public Wi-Fi networks (such as free WiFi in Airports or cafes), which are often less secure, a VPN ensures that the data remains shielded from potential threats.
Defence in Depth
Defence in Depth is a cybersecurity strategy that emphasises the importance of having multiple layers of security measures in place to protect your digital assets. It operates on the principle that if one layer of security fails, there are additional layers ready to prevent or mitigate potential threats.Think of it as building a series of concentric barriers around your valuable digital assets. Each barrier represents a distinct security layer, and together, they create a formidable defence. Here's how Defence in Depth works:
- Multiple Layers: Instead of relying on a single security solution, you implement several layers of protection throughout your digital environment. These layers can include firewalls, access controls, network segmentation, encryption, and more.
- Redundancy: Each security layer acts as a backup to the others. If one layer is breached or compromised, the remaining layers continue to provide protection. It's similar to having multiple locks on a door - if one lock is picked, others still secure the entrance.
- Comprehensive Coverage: The various layers address different aspects of security, such as network security, access control, data protection, and user training. This ensures that potential vulnerabilities are covered from multiple angles.
- Minimising Risk: Defence in Depth reduces the likelihood of a successful cyberattack. Even if an attacker manages to breach one layer, they face additional challenges as they progress through the remaining layers.
- Adaptability: The strategy can adapt to evolving threats. As new threats emerge, administrators can add or adjust security layers to stay ahead of potential risks.
Zero Trust
The Zero Trust model represents a fundamental shift in the way organisations approach cybersecurity. Unlike traditional security models, which often rely on perimeter defences and assume trust within the network, Zero Trust flips this notion entirely. At its core, Zero Trust operates on the principle of "never trust, always verify."Imagine an organisation's digital environment as a highly secure vault, and each user or device trying to access it as a visitor. In a traditional model, once a visitor is inside the vault's walls, they are often granted free access to move around. However, in the Zero Trust model, visitors are met with locked doors at every step, and they must continuously prove their identity and intentions before gaining access.
Key components of the Zero Trust model include:
- Identity Verification: Every user, device, or system seeking access must first prove their identity. This is typically done through strong authentication methods, such as multi-factor authentication (MFA), smart cards, or biometrics.
- Least Privilege: Users and devices are only granted the minimum level of access required to perform their tasks. This principle ensures that even if a user's credentials are compromised, the potential damage is limited.
- Micro-Segmentation: The network is divided into small, isolated segments. Each segment has its own security controls and access rules. This prevents lateral movement by attackers within the network, even if they breach one segment.
- Continuous Monitoring: Once granted access, users and devices are continuously monitored for suspicious behaviour. Any deviations from normal activities trigger alerts and potential access restrictions.
- Encryption: Data is encrypted both in transit and at rest to protect it from eavesdropping and unauthorised access.
In a world where cyber threats are continually evolving, Zero Trust offers a proactive and robust approach to cybersecurity, mitigating the risks associated with the assumption of trust and bolstering an organisation's overall resilience against cyberattacks.
Network Access Control (NAC)
Network Access Control (NAC) is a pivotal element in the arsenal of modern cybersecurity. At its core, NAC is all about ensuring that only trusted and compliant devices gain access to an organisation's network resources. It's like having a vigilant gatekeeper who scrutinises everyone seeking entry to your digital realm and only grants access to those who meet the stringent security requirements.NAC functions as a series of checkpoints, each with specific criteria that devices must meet before proceeding. Here's how NAC works:
- Security Policy: Organisations establish a security policy that outlines the rules and requirements for devices seeking network access. This policy may include factors such as up-to-date antivirus software, operating system patches, and secure configurations.
- Device Assessment: When a device attempts to connect to the network, it undergoes a thorough assessment. This evaluation checks whether the device adheres to the security policy. If the device fails to meet these criteria, it's either denied access or placed in a restricted area with limited privileges.
- Authentication: NAC often incorporates robust authentication methods to verify the identity of the device and its user. This can include multi-factor authentication, digital certificates, or user credentials.
- Continuous Monitoring: Once granted access, devices are continuously monitored. If a device's compliance status changes or suspicious activity is detected, NAC can respond by re-evaluating or restricting the device's access.
- Segmentation: NAC can also be used in conjunction with network segmentation, where devices are placed into isolated segments with specific security policies. This further limits the potential impact of security breaches.
Secure Wi-Fi
Wi-Fi is the lifeblood of many organisations’s digital connectivity, enabling people to work, play, and communicate wirelessly. However, an unsecured Wi-Fi network is often a door wide open to potential intruders. As such, it is crucial to implement secure Wi-Fi practices.- Strong Credentials: Access to a Wi-Fi network should not be done with a shared login password but with unique username and password for each users. It allows better security and accountability.
- WPA2 / WPA3 Encryption: The latest encryption standard, WPA2 or WPA3, must be used to protect Wi-Fi network. This technology encrypts the data transmitted between your devices and the router, making it nearly impossible for unauthorised individuals to intercept and decipher. Previous versions of WPA, or other Wi-Fi security protocols such as Wi-Fi Protected Setup (WPS), are now considered insecure.
- Network Name (SSID): The network name, also known as the SSID, should not reveal any personal information. It should avoid using the organisation name or address. A generic name is often a safer choice.
- Guest Network: Visitors should not be authorised to access the same networks as employees. As such, a separate guest network for guest is a sensible approach. This network should have limited access to your main network resources, preventing guests from inadvertently accessing sensitive data.
Data Centres and Physical Networks
Securing a data centre and its physical network is paramount to maintain the integrity and availability of critical digital assets. Several essential aspects contribute to this comprehensive security approach:- Power Redundancy: Reliable and redundant power sources are the lifeblood of a data centre. Dual power feeds, backup generators, and uninterruptible power supplies (UPS) ensure continuous operation, even during electrical outages. This redundancy is akin to having multiple layers of safety nets to catch any power failures.
- HVAC Control: The data centres environment is delicately controlled to ensure servers and networking equipment operate optimally. Proper temperature and humidity levels are maintained using advanced Heating, Ventilation, and Air Conditioning (HVAC) systems. Think of it as climate control for your digital infrastructure, preventing overheating and equipment damage.
- Fire Suppression: Implementing robust fire suppression systems is like having an automated firefighter on standby. These systems use various methods, such as gas-based or water-based suppression, to extinguish fires quickly without causing damage to the equipment. Fire suppression is crucial in a data centre, where a fire could lead to catastrophic data loss.
- Redundancy: Redundancy is the safety net within a safety net. It involves having backup systems for every critical component. Redundant servers, storage arrays, network switches, and data paths ensure seamless operation even if a primary component fails. It's similar to having a spare tire in your car; if one goes flat, you can keep moving.
- MOU/MOA (Memorandum of Understanding/Memorandum of Agreement): These agreements outline how different parties, such as data centre operators and their clients, cooperate and share resources. They establish expectations and responsibilities, ensuring everyone is on the same page regarding security, access, and maintenance.
Conclusion
In an era where information is the lifeblood of organisations and individuals alike, network security has emerged as an indispensable fortress against an onslaught of digital threats. The landscape of network security is intricate and ever-evolving, reflecting the dynamic nature of cyber threats.From the pernicious spread of malware to the cunning tactics of hackers, and the potential risks posed by insiders, the modern network faces multifaceted challenges. However, knowledge is power, and understanding these threats is the first crucial step in erecting an effective defence.
This article has illuminated the key concepts, tools, and strategies within the realm of network security. We've explored the importance of identifying and mitigating threats using tools like Intrusion Detection Systems (IDS) and firewalls, emphasising the need for a multi-layered approach.
Moreover, we've ventured into the realm of secure network design, examining principles such as network segmentation, Zero Trust, and Network Access Control (NAC). These concepts provide a blueprint for building resilient networks that can withstand even the most determined adversaries.
Secure Wi-Fi practices were also addressed, as the ubiquity of wireless networks in modern life makes them a prime target for cyberattacks. By following best practices in Wi-Fi security, organisations can ensure the safety of their data and digital infrastructure.
Lastly, we delved into the physical security of data centres, where power redundancy, HVAC control, fire suppression, and redundancy of critical components combine to protect the heart of digital operations.
In today's interconnected world, network security is not just a choice; it's a necessity. With the knowledge gained from this exploration, individuals and organisations alike are better equipped to navigate the complex landscape of network security, fortify their digital assets, and guard against the relentless tide of cyber threats. Remember, in the realm of network security, vigilance and preparation are paramount, for only by staying one step ahead can we ensure the safety and integrity of our digital domain.
Check your readiness with a Quiz: https://forms.office.com/r/7YqW4XSQAu
Disclamer: This article is not legal or regulatory advice. You should seek independent advice on your legal and regulatory obligations. The views and opinions expressed in this article are solely those of the author. These views and opinions do not necessarily represent those of HSBC or its staff. Artificial Intelligence Technology was used to read-proof this article.