🔐 Key Security Principles
This article is part 1 (of 6) of a series to help you prepare for the ISC2 Certified in Cybersecurity (CC) certification.
The CC certification is a foundational certification that covers the core concepts and principles of cybersecurity. It is designed for anyone who wants to enter or progress in the cybersecurity field, regardless of their background or experience.
🎓 Become Certified in CyberSecurity series: https://www.jbbres.com/files/cc-2023.html
🎓 ISC2 Certified in Cybersecurity (CC): https://www.isc2.org/Certifications/CC
Information Security refers to the practice of protecting information from unauthorised access, use, disclosure, disruption, modification, or destruction. It is an essential aspect of any organisation that deals with sensitive data, such as personal information, financial data, or intellectual property.
In this article, we will cover the key principles of information security in a way that is accessible to individuals without a technical background. More specifically, we will be covering 5 key principles:
- The CIA triad (confidentiality, integrity, and availability), where we will explain how these 3 concepts form the basis of information security .
- Risk Management, where we will explore how organisations can assess and prioritise risks, and decide on appropriate risk response strategies.
- Security Controls, where we will introduce the different types of security controls (physical, technical, and administrative) that organisations can implement to protect their information.
- Governance, where we will discuss the policies, procedures, and regulations that shape organisational management and drive decision-making in information security.
- Finally, we will look the ISC2 code of conduct, which defines the standards for ethical and professional behaviour that are expected of information security professional.
Confidentiality, Integrity and Availability: The CIA Triad
Protecting sensitive information is crucial for any organisation. Whether it is personal information, financial data, or intellectual property, it is essential to ensure that data is kept secure and protected from cyber threats. The concept of information security is all about safeguarding data by ensuring its confidentiality, integrity, and availability, also known as the CIA triad.The CIA triad is the foundation of information security , and it comprises the three essential elements (confidentiality, integrity, and availability) that work together to protect data. These elements provide the framework for organisations to ensure the protection of their sensitive data.
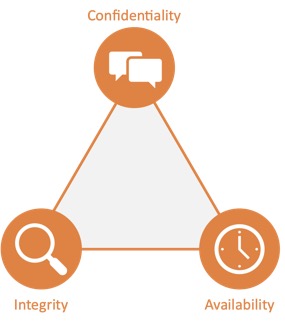
- Confidentiality refers to the protection of data that needs to be kept confidential. This includes any data that should not be disclosed to unauthorised individuals, such as personal information, financial data, and trade secrets. Confidentiality measures can include encryption, access controls, and user authentication, which can help prevent unauthorised access to data.
- Integrity ensures that data is not altered in an unauthorised manner. This means that data should remain accurate and complete, and any changes to the data should be authorised and recorded. Ensuring the integrity of data is crucial for organisations that rely on accurate and reliable data to make decisions. Measures to ensure data integrity include data validation and checksums, which can help detect any unauthorised changes to the data.
- Availability refers to ensuring that data is accessible to authorised users when and where it is needed, and in the form and format that is required. This means that data should be available to users when they need it and should not be inaccessible due to system failures or cyber-attacks. Availability measures can include redundancy, backups, and disaster recovery plans, which can help ensure that data is always available when it is needed.
You can see the CIA triad as a framework for information security . Confidentiality ensures that data is protected from unauthorised access, integrity ensures that data is not altered in an unauthorised manner, and availability ensures that data is accessible to authorised users when and where it is needed. By ensuring the CIA triad, organisations can protect their sensitive data from cyber threats and ensure that their data remains secure and reliable.
Non-repudiation
Another key element in Information Security is the concept of non-repudiation. Non-repudiation is the ability to prove that a message or action was actually sent or performed by the party claiming to have sent or performed it, and that the party cannot deny having done so later on. Non-repudiation is important in information security because it helps ensure accountability and prevent disputes or legal issues related to denial of responsibility.In order to achieve non-repudiation, there are typically three key requirements:
- Authentication: Ensuring that the party sending or performing the action is who they claim to be.
- Integrity: Ensuring that the message or action has not been altered or tampered with in transit.
- Auditing: Keeping a record of the transaction, including any relevant metadata (such as timestamps and digital signatures), to provide evidence of what happened and when.
One common example of non-repudiation is digital signatures. A digital signature is a mathematical scheme for verifying the authenticity of digital messages or documents. It ensures that the message was sent by the person who claims to have sent it and that the message has not been tampered with in transit. Digital signatures are commonly used in e-commerce transactions and other situations where the authenticity of the message is critical.
Another example of non-repudiation is in email communication. When sending an email, a digital signature can be added to the message to ensure that the recipient can verify that the message came from the sender and that the message has not been altered in transit. Additionally, email servers may keep logs of all incoming and outgoing messages, providing an audit trail that can be used to verify the authenticity of the message and the identity of the sender.
Overall, non-repudiation is an important aspect of information security, providing a way to ensure accountability and prevent disputes or legal issues related to denial of responsibility. By implementing measures such as digital signatures and auditing, organisations can increase their level of non-repudiation and ensure that their communication and transactions are secure and reliable.
Privacy
Privacy refers to an individual's right to control their personal information and how it is collected, used, shared, and stored. In the context of information security, privacy is an important consideration because organisations collect and store vast amounts of personal information about their customers, employees, and partners. This information can include names, addresses, social security numbers, credit card numbers, and other sensitive data.Privacy is protected by laws and regulations that govern how personal information is collected, used, and shared. For example, the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) are two important laws that protect the privacy of individuals. These laws require organisations to obtain explicit consent from individuals before collecting their personal information, and they provide individuals with the right to access, correct, and delete their personal information. In Australia, privacy is protected by the Privacy Act 1988.
To protect privacy, organisations must implement appropriate security controls to prevent unauthorised access to personal information. This might include measures such as encryption, access controls, and data backup and recovery. Organisations must also have policies and procedures in place to ensure that personal information is collected, used, and shared in accordance with applicable laws and regulations.
Privacy is becoming increasingly important as more organisations collect and store vast amounts of personal information. A privacy breach can have serious consequences for both individuals and organisations. For example, a company that experiences a data breach can face financial penalties, loss of customer trust, and damage to its reputation. Individuals whose personal information is compromised can be at risk of identity theft, financial fraud, and other forms of harm.
Privacy is an important aspect of information security that requires organisations to protect personal information and ensure that it is collected, used, and shared in accordance with applicable laws and regulations. By implementing appropriate security controls and policies and procedures, organisations can protect the privacy of individuals and maintain their trust and confidence.
Risk Management
In today's interconnected world, information is a valuable asset that organisations must protect from various risks and threats. These risks and threats can come in many forms, such as cyber-attacks, natural disasters, human error, and other unforeseen events. Therefore, organisations must adopt a systematic approach to assess and manage these risks to protect their valuable assets and ensure business continuity.Risk management is the process of identifying, assessing, and prioritising and implementing strategies to mitigate or transfer them. It is a continuous process that involves ongoing monitoring and reassessment of risks and the effectiveness of risk management strategies.
The risk management process is usually comprised of 3 steps:
- Risk identification: identifying potential threats and vulnerabilities.
- Risk assessment: estimate impact and likelihood of a risk.
- Risk treatment: decide on the appropriate risk response.
Risk Identification
To manage risk, the first step is to identify potential threats and vulnerabilities. In the context of cybersecurity, threat actors are individuals or groups who seek to exploit vulnerabilities in an organisation's information system for personal gain or malicious intent. Threat actors can come from a variety of sources:- Insiders can be a significant threat, as they have access to sensitive information and may have malicious intent, act through simple human error, or due to gross incompetence. For example, an employee who intentionally accesses and shares sensitive data with unauthorised individuals can compromise an organisation's confidentiality.
- Outside individuals or informal groups can be opportunistic or planned attackers, who may discover vulnerabilities through various means, including social engineering or technical exploits. They may be motivated by financial gain or other malicious intentions.
- Formal entities that are non-political, such as business competitors and cybercriminals, may also pose a significant threat to an organisation's information security. These attackers may use sophisticated techniques and tools to exploit vulnerabilities, and their motives may include financial gain or other objectives.
- Formal entities that are political, such as terrorists, nation-states, and hactivists, may use cyberattacks to achieve their political goals or disrupt an organisation's operations.
- Intelligence or information gatherers, who may be any of the above, also pose a significant threat to organisations. They may use various techniques to gather sensitive information, including social engineering or technical exploits.
- Finally, technology itself, such as free-running bots and artificial intelligence, can be part of any of the above categories and may pose a significant threat to an organisation's information security.
Vulnerabilities are weaknesses in a system that a treat might exploit to undermine the confidentiality, integrity or availability of the organisation. Vulnerabilities might include missing patches or misconfiguration.
Risks occur when an environment contains both a vulnerability and a corresponding threat that might exploit that vulnerability. For example, if a company forget to update their antivirus signatures on their workstations and hackers release a new virus upon the internet, the organisation faces a risk. It is vulnerable because it is missing a security control, and there is a threat: the new virus.
Risk Assessment
Once risks have been identified, the next step is to assess them. This involves estimating and prioritising risks to an organisation’s operations (including its mission, functions, image, and reputation), assets, individuals, and other organisations (even the nation). The risk assessment process should result in aligning (or associating) each identified risk resulting from the operation of an information system with the goals, objectives, assets, or processes of the organisation.One common method for prioritising risks is the likelihood (or probability) and impact model. This model involves assessing the likelihood of a risk occurring and the potential impact if it does occur. For example, a hospital might identify the risk of a cyberattack on its patient data. The hospital might estimate that the likelihood of a successful attack is high, and that the impact would be severe. Based on this assessment, the hospital might prioritise this risk as a high priority and take steps to mitigate it.
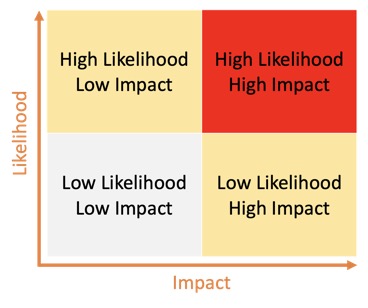
A tool used for such assessment is a risk prioritisation matrix. It helps organisations determine which risks to prioritise for action based on their likelihood and potential impact. The matrix typically divides risks into three categories: high priority, medium priority, and low priority. For example, a bank might use a risk prioritisation matrix to determine that a phishing attack on its customers is a high priority risk, while a minor software vulnerability is a low priority risk.
Risk Treatment
After risks have been identified, assessed, and prioritised, organisations can decide on appropriate risk response strategies. These strategies might include:- Accept the risk: Risk acceptance (sometime also called risk tolerance) is taking no action to reduce the likelihood of a risk occurring. For example, a small business might accept the risk of a data breach because the cost of implementing additional security measures is too high.
- Avoid the risk: Risk avoidance is the decision to attempt to eliminate the risk entirely. For example, a company might avoid the risk of a cyberattack by discontinuing the use of a particular software program that is known to have vulnerabilities.
- Mitigate (i.e. reduce) the risk: Risk mitigation is the most common type of risk management and includes taking actions to prevent or reduce the possibility of a risk event or its impact. For example, a company might mitigate the risk of a data breach by implementing two-factor authentication for all user accounts.
- Transfer or share the risk: Risk transference is the practice of passing the risk to another party, who will accept the financial impact of the harm resulting from a risk being realised in exchange for payment. For example, an insurance company might offer cybersecurity insurance to a business, transferring the risk of a cyberattack to the insurance company.
Managing information security risks requires a systematic approach that includes identifying and assessing risks, prioritising risks based on their probability and impact, and selecting appropriate risk response strategies. By following these steps, organisations can reduce the likelihood and impact of security incidents and protect their valuable assets, reputation, and customers.
The Risk Management Process enables organisations to assess and prioritise risks and decide on appropriate risk response strategies. Organisations should have a systematic approach to identifying risks, assessing their potential impact, and deciding on appropriate risk response strategies.
Security controls
In order to mitigate an information security risk, organisations put in place measures to safeguard their systems and data. These measures are called security controls. There are three main types of security controls: physical, technical, and administrative.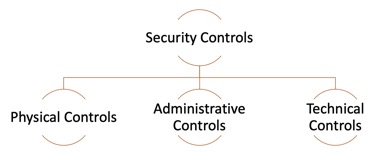
Physical controls
Physical controls are hardware devices and architectural features that address process-based security needs. Physical controls aim to physically prevent or detect unauthorised access, damage, or interference to information systems. Examples of physical controls include:- Badge readers and access control systems that restrict physical access to authorised personnel only
- Fences and walls that protect facilities from unauthorised access
- Cameras and surveillance systems that monitor physical locations for unusual activity
- Fire suppression systems that protect against loss or damage from fires
- Backup generators that ensure continuity of operations during power outages
Technical controls
Technical controls, also known as logical controls, are security measures that computer systems and networks implement directly. Technical controls aim to protect data in storage, data in transit, and data in use. Examples of technical controls include:- Firewalls that monitor and filter incoming and outgoing network traffic
- Encryption that protects data by making it unreadable without the correct decryption key
- Antivirus software that detects and prevents malware infections
- Intrusion detection and prevention systems that monitor networks for suspicious activity
- Access controls that restrict access to data based on user permissions
- Two-factor authentication that requires a user to provide two forms of identification before accessing a system or data
Administrative controls
Administrative controls, also known as managerial controls, are directives, guidelines, or advisories aimed at people within the organisation. Administrative controls aim to promote good security practices and ensure that employees are following security policies and procedures. Examples of administrative controls include:- Security policies that outline the rules and guidelines for protecting information
- Security training that educates employees on how to identify and respond to security threats
- Security audits that assess an organisation's security posture and identify areas for improvement
- Background checks that screen employees for criminal history and other potential security risks
- Incident response plans that outline how to respond to security incidents and minimise their impact
By implementing physical, technical, and administrative controls, organisations can reduce their risk of security incidents and protect their information systems and data.
Governance
Information security governance refers to the system of policies, procedures, and regulations that an organisation puts in place to manage and protect its sensitive information. There are several key elements to information security governance that organisations must consider:- Policies: Policies are put in place by organisational governance, such as executive management, to provide guidance to all activities to ensure that the organisation supports industry standards and regulations. Policies are typically broad in scope and provide an overarching framework for how the organisation should approach information security. Examples of policies might include a password policy that mandates strong passwords or an access control policy that outlines who should have access to what information.
- Standards: Standards are often used by governance teams to provide a framework to introduce policies and procedures in the organisation. Standards are typically more specific than policies and provide guidance on how to implement security controls. For example, an organisation might use the ISO 27001 standard to help them implement an information security management system (ISMS).
- Procedures: Procedures are the detailed steps needed to complete a specific task, such as how to implement and manage security controls. Procedures should support departmental or organisational policies and be updated as needed. For example, an organisation might have a procedure in place for creating and managing user accounts that includes steps for verifying identity and setting appropriate permissions.
- Regulations and Laws: Regulations are commonly issued in the form of laws, usually from government, and typically carry financial penalties for non-compliance. Regulations set out specific requirements that organisations must adhere to, and failure to comply can result in legal consequences. Here are some examples of regulations that organisation might have to adhere to depending on their location or field of work:
- the European Union's General Data Protection Regulation (GDPR) requires organisations to protect the personal data of EU citizens and imposes severe financial penalties for non-compliance.
- The HIPAA (Health Insurance Portability and Accountability Act) is a US requirement for healthcare organisations to implement specific administrative, physical, and technical safeguards to protect the confidentiality, integrity, and availability of patient data.
- The SOX (Sarbanes-Oxley Act) requires US public companies to implement specific controls and processes to ensure the accuracy and integrity of financial information.
- APRA CPS 234 mandates Australian financial institutions to establish robust cybersecurity frameworks, ensuring the security and resilience of sensitive data against cyber threats.
Overall, these governance elements work together to create a framework for effective information security management, ensuring that organisations comply with applicable regulations, adopt industry best practices, and manage risk effectively.
ISC2 Code of Ethics
If you are reading this article in preparation of the ISC2 Certification in Cyber-Security, you also need to be aware of the ISC2 Code of Ethics.ISC2, the International Information System Security Certification Consortium, is a nonprofit organisation that provides education and certification in the field of information security. Its Code of Ethics sets the standards for ethical and professional behaviour that are expected of its members.
The Code of Ethics begins with a preamble that highlights the importance of adhering to the highest ethical standards of behaviour. It emphasises the responsibility that members have to protect society, the common good, public trust, and the infrastructure.
The ISC2 member is expected to act honourably, honestly, justly, responsibly, and legally. This means they must provide competent and diligent service to their principals, and they must not engage in any activity that could harm society, the public, or the infrastructure.
The ISC2 Code of Ethics provides a framework for ethical decision-making in the field of information security. It requires that members act with integrity, honesty, and responsibility in all aspects of their professional and personal lives. Violations of the Code of Ethics can result in disciplinary action, including the loss of certification.
Examples of violations of the Code of Ethics include engaging in unethical behaviour, such as hacking into computer systems, stealing confidential information, or engaging in fraudulent activity. It also includes failing to report security breaches or other incidents that could harm society, the public, or the infrastructure.
In summary, the ISC2 Code of Ethics provides a set of guidelines that members of the information security community must follow to ensure they act in an ethical and professional manner. Adhering to the Code of Ethics helps to maintain public trust and confidence in the profession, and it ensures that members of the information security community are held to the highest standards of behaviour.
Conclusion
Information security is a crucial aspect of modern organisations, particularly as more and more business processes are becoming digitalised. In this article, we have discussed some of the fundamental concepts and practices that underpin information security , such as the CIA triad, risk management, security controls, governance elements, and Ethics.By implementing the practices discussed in this article, organisations ensure that their sensitive data and critical systems are protected from cyber threats and other risks. Ultimately, effective information security requires a holistic approach that involves people, processes, and technology, and that is continuously reviewed and updated in light of changing threats and business needs.
Check your readiness with a Quiz: https://forms.office.com/r/tqn18kS8A5
Disclamer: This article is not legal or regulatory advice. You should seek independent advice on your legal and regulatory obligations. The views and opinions expressed in this article are solely those of the author. These views and opinions do not necessarily represent those of HSBC or its staff. Artificial Intelligence Technology was used to read-proof this article.