🔐 Network Concepts
This article is part 4 (of 6) of a series to help you prepare for the ISC2 Certified in Cybersecurity (CC) certification.
The CC certification is a foundational certification that covers the core concepts and principles of cybersecurity. It is designed for anyone who wants to enter or progress in the cybersecurity field, regardless of their background or experience.
🎓 Become Certified in CyberSecurity series: https://www.jbbres.com/files/cc-2023.html
🎓 ISC2 Certified in Cybersecurity (CC): https://www.isc2.org/Certifications/CC
In today's interconnected world, computer networks serve as the digital highways that facilitate the exchange of information, resources, and data. They form the backbone of modern communication, enabling everything from casual internet browsing to intricate corporate infrastructures and global data transmission. While the concept of computer networks may appear straightforward at its core—connecting multiple devices—it encompasses a rich tapestry of intricacies and diversity.
Within the realm of computer networking, various types of networks have emerged, each tailored to specific needs and scenarios. From the intimate confines of your home to the vast expanse of the World Wide Web, these networks underpin the way we live and work. Moreover, the hardware and protocols that make these networks function seamlessly are equally critical.
In this comprehensive exploration of computer network concepts, we will delve into the types of networks that define our digital landscape, understand the vital role played by network devices, decipher the significance of IP addresses and DHCP, and shed light on the essential role of network ports. Furthermore, we will unravel key network terms, elucidate the models governing network communication, and decode the intricate protocols that power our interconnected world.
By the end of this article, you will have a profound understanding of the intricate web of technologies that make the modern digital age possible, and how they shape the way we connect, communicate, and collaborate. So, let's embark on this exploration of computer networks, where the digital meets the practical, and where the possibilities are as boundless as the information they carry.
Type of computer networks
At its core, a computer network is simply two or more computers linked together to share data, information or resources. However, not all networks are created equal. There are many different types of networks, each with its own set of characteristics and uses.When it comes to computer networking, there are several types of networks that serve different purposes. Here are some of the most common types of networks:
- PAN (Personal Area Network): This is a network that connects devices that are in close proximity to each other, usually within a few meters. Examples of devices that might be connected in a PAN include a computer and a wireless mouse or keyboard.
- LAN (Local Area Network): This is a network that connects devices within a limited geographical area, such as a home, office building, or school campus. For example, a LAN might connect all the computers and printers in a small business. LAN are sometime referred with the type of connection they use, for example:
- WLAN (Wireless Local Area Network): This is a type of LAN that uses wireless technology (like Wi-Fi) instead of cables to connect devices. A WLAN is often used in situations where it's not practical or possible to run cables, such as in a coffee shop or airport.
- POLAN (Passive Optical Local Area Network): This is a type of LAN that uses fibre optic cables to connect devices. POLAN is often used in large buildings or campuses.
- CAN (Campus Area Network): This is a network that connects multiple buildings within a university or business campus. For example, a CAN might connect all the buildings on a college campus.
- MAN (Metropolitan Area Network): This is a network that covers a larger area than a LAN, but smaller than a WAN. It's often used by organisations or businesses that have multiple locations within a city or region.
- WAN (Wide Area Network): This is a network that connects devices over a larger geographical area, such as between different cities, states, or countries. For example, a WAN might connect all the offices of a multinational corporation. the Internet the world's largest WAN.
- SAN (Storage Area Network): This is a network that connects data storage devices, such as hard drives or tape libraries, to servers.
- VPN (Virtual Private Network): This is a secure network that connects devices over the internet. A VPN is often used by remote workers to access a company's internal network from outside the office.
- EPN (Enterprise Private Network): This is a network that connects multiple locations of an organisation. EPN is similar to a WAN but is designed specifically for a single organisation.
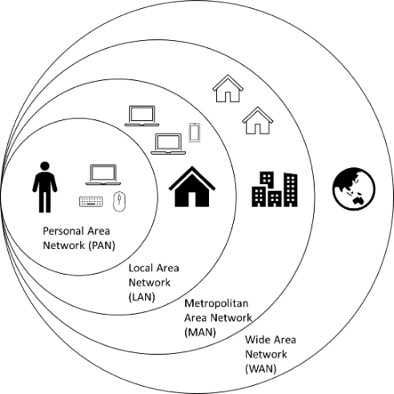
By understanding the different types of networks and their uses, you can better understand how computer networking works and how you can use it in your personal or professional life.
Network TechnologyNetwork DevicesNetworks are not just composed of cables running from point to point to connect computers. In order to direct the traffic and ensure communications are optimised, a number of network devices are presents as intermediary relay. The most common devices you will see operating a network are:
- Hubs: Hubs are used to connect multiple devices together in a network. They work by broadcasting data to all devices connected to them, which can lead to network congestion and slow performance.
- Switches: Switches are used to connect devices in a network, like hubs. However, unlike hubs, switches can send data to specific devices on the network, which makes them more efficient and reduces network congestion.
- Repeaters: Repeaters are used to amplify or regenerate signals that are transmitted over long distances. They are often used to extend the range of wireless networks.
- Routers: Routers are used to connect multiple networks together. They are responsible for directing data between different networks, ensuring that data packets reach their intended destinations.
- Bridges: Bridges are used to connect two networks together, like routers. However, unlike routers, bridges work at the data link layer of the OSI model, which means they are used to connect two networks that use the same protocol.
- Gateways: Gateways are devices that are used to connect networks that use different protocols or communication standards. They are often used to connect local area networks to the internet.
- Modems: Modems are used to connect computers and other devices to the internet over a telephone line or other communication channel.
- Firewalls: Firewalls are used to protect networks from unauthorised access and cyber threats. They filter out incoming and outgoing network traffic, based on a set of predetermined security rules.
- Access points: Access points are devices that are used to connect wireless devices to a wireless network.
- Endpoints: Endpoints are devices that are used by end-users to connect to a network, such as desktop computers, laptops, tablets, mobile phones, and VOIP phones.
- Servers: Servers are computers that are used to provide specific services to other devices on the network. For example, a file server is used to store and share files across the network.
- Printers: Printers are devices that are used to print documents or other materials from a computer or other device on the network.
- Internet of Things (IoT): IoT devices are physical objects embedded with sensors, software, and connectivity capabilities that enable them to collect, transmit, and receive data over the internet or other networks.
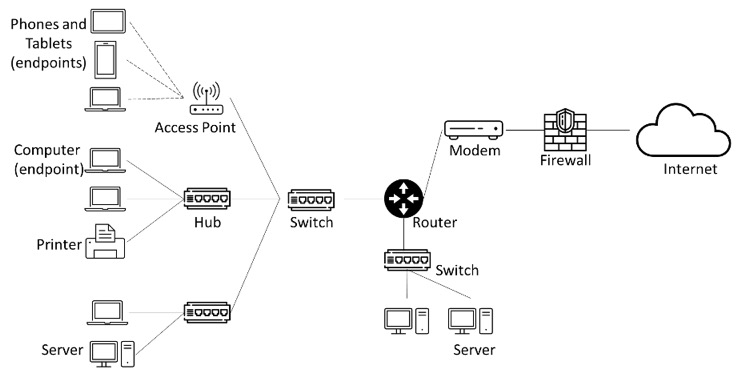
- Bridges: Bridges are used to connect two networks together, like routers. However, unlike routers, bridges work at the data link layer of the OSI model, which means they are used to connect two networks that use the same protocol.
- Gateways: Gateways are devices that are used to connect networks that use different protocols or communication standards. They are often used to connect local area networks to the internet.
- Modems: Modems are used to connect computers and other devices to the internet over a telephone line or other communication channel.
- Servers: Servers are computers that are used to provide specific services to other devices on the network. For example, a file server is used to store and share files across the network.
- Printers: Printers are devices that are used to print documents or other materials from a computer or other device on the network.
- Internet of Things (IoT): IoT devices are physical objects embedded with sensors, software, and connectivity capabilities that enable them to collect, transmit, and receive data over the internet or other networks.
Each of these devices plays a critical role in ensuring that a network is functional and secure. By understanding the role of each device, you can better design and manage your network to meet the needs of your organisation.
IP Addresses and DHCP
An IP (Internet Protocol) address is a unique numerical identifier assigned to each device on a network. It allows devices to be identified and located on the internet or within a private network. Think of it like a phone number for a computer or other device.In the past, the most common type of IP address was IPv4, which used a 32-bit address format and allowed for about 4 billion unique addresses.
To simplify things, IPv4 addresses are typically written in a dotted-decimal notation, where four groups of numbers separated by dots represent the different parts of the IP address. For example, an IPv4 address might look like 192.168.0.1.
However, with the rapid growth of the internet and more devices being connected, IPv4 addresses are becoming scarce.
IPv6 is a newer and more modern version of IP addressing, which uses a 128-bit address format and allows for a significantly larger number of unique addresses. This makes it possible to assign unique addresses to every device on the planet, and then some. IPv6 also provide improved security and quality of service.
IPv6 addresses are typically written as height groups of numbers and letters separated by semi-columns. IPv6 address might look like 2001:0db8:85a3:0000:0000:8a2e:0370:7334.
DHCP (Dynamic Host Configuration Protocol) is a technology that simplifies the process of assigning IP addresses to devices on a network.
Instead of manually configuring each device's IP address, DHCP automatically assigns IP addresses to devices as they connect to the network. It ensures that each device receives a unique IP address and helps manage the network's available IP addresses efficiently.
DHCP makes it easier to set up and manage networks by automating the IP address assignment process, reducing the chances of address conflicts, and minimising the need for manual configuration. Typically, servers are configured with static IP, so they always keep the same address, and end user devices are configured with dynamically changing IP addresses, meaning that they might get a different IP address every time they reconnect to a given network.
In summary, IP addresses are unique numerical labels assigned to devices for communication purposes. IPv4 is the original IP addressing system but has limitations on available addresses, while IPv6 is the newer version designed to provide a vast pool of addresses. DHCP simplifies IP address assignment by automatically assigning addresses to devices on a network, making network setup and management easier.
Network Ports
In computer networking, network ports are virtual communication endpoints that allow different applications and services to interact with each other. Think of ports as doors in a computer that allow access to different services. Each port, or door, lead to a specific room where different activities take place. Each port is assigned a unique number, and applications use these numbers to send and receive data over a network.Port numbers range from 0 to 65535 and are divided into three categories:
- Well-Known Ports: These ports are numbered from 0 to 1023 and are reserved for specific services commonly used in the industry. Here are a few examples:
- Port 80: This port is used for HTTP (Hypertext Transfer Protocol) traffic. When you browse the internet and enter a website address, your web browser typically communicates with the web server using port 80.
- Port 443: This port is used for secure web traffic over HTTPS (Hypertext Transfer Protocol Secure). It is commonly used for online banking, e-commerce websites, and other secure online transactions.
- Port 25: This port is used for SMTP (Simple Mail Transfer Protocol), which handles email delivery between servers.
- Registered Ports: Ports in the range of 1024 to 49151 are known as registered ports. These ports are used by specific applications or services but are not as universally recognised as well-known ports. Examples include:
- Port 3306: This port is commonly used for MySQL database connections.
- Port 8080: This port is often used as an alternative to port 80 for web traffic, especially for testing or running web applications locally.
- Dynamic/Private Ports: The range from 49152 to 65535 is reserved for dynamic or private ports. These ports are used for temporary connections and are dynamically assigned by the operating system.
Network ports play a crucial role in enabling communication between different devices and services on a network. They ensure that data is sent to the correct application or service running on a specific device. By using different port numbers, applications can effectively separate and manage their network traffic, allowing multiple services to coexist and function independently.
Understanding common port numbers used in the industry can help in troubleshooting network issues, configuring firewalls, or ensuring that specific services are accessible. While this is just a brief introduction to network ports, it highlights their significance in facilitating communication between devices and applications across a network.
Others Network Terms
Here's a brief explanation of some additional of the network terms:- Packet: A packet is a unit of data that is transmitted over a network. It consists of a header, which contains information about the packet's source, destination, and other details, and a payload that carries the actual data being sent.
- Protocol: A protocol is a set of rules and guidelines that govern the communication between devices on a network. It defines how data is transmitted, received, and interpreted, ensuring compatibility and seamless communication between different devices and systems.
- Ethernet: Ethernet is a widely used networking technology that allows devices to connect and communicate over a local area network (LAN). It provides a set of standards for wired network connections, specifying how data is transmitted and received over Ethernet cables.
- Wi-Fi: Wi-Fi is a wireless networking technology that allows devices to connect to a network without the need for physical cables. It uses radio waves to transmit and receive data, enabling wireless internet access and local network connectivity.
- MAC address: A MAC (Media Access Control) address is a unique identifier assigned to the network interface of a device. It is a hardware-based address that is permanently assigned during manufacturing and is used for identifying devices on a local network. MAC addresses are primarily used at the data link layer of the OSI model.
Network Models
The OSI (Open Systems Interconnection) model and TCP/IP (Transmission Control Protocol/Internet Protocol) model are two protocols that define how data is transmitted over a network.The OSI model encapsulates data by adding a header and footer to each layer as it moves through the network. The header and footer contain information needed for that particular layer to function and are removed at the receiving end. This process ensures that the data is delivered correctly and helps to prevent errors or data loss.
The OSI model consists of seven layers, each responsible for a specific aspect of network communication. The layers are:
- Physical layer - This layer is responsible for the physical transmission of data over the network. It defines the electrical and physical specifications of the network components, such as cables and network cards. Over the physical layer, data are exchanged as bit (0 and 1).
- Data link layer - This layer is responsible for the logical transmission of data over the network. It provides error detection and correction to ensure data integrity and reliability.
- Network layer - This layer is responsible for routing data through the network, using logical addressing and routing protocols.
- Transport layer - This layer provides end-to-end data delivery and error recovery between network devices.
- Session layer - This layer establishes, manages, and terminates sessions between devices. It also manages data exchange synchronisation and maintains session state information.
- Presentation layer - This layer ensures that data is presented in a format that can be understood by the application layer. It handles data compression, encryption, and decryption.
- Application layer - This layer provides network services to end-users and applications, such as file transfer, email, and web browsing.
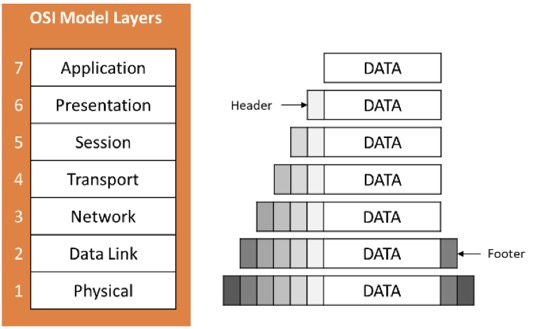
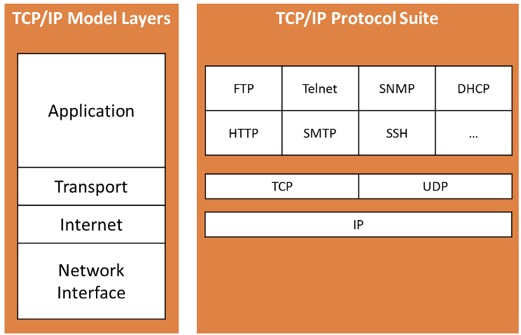
On the other hand, the TCP/IP model consists of four layers:
- Network interface layer - This layer is responsible for transmitting data between network devices, using protocols such as Ethernet.
- Internet layer - This layer is responsible for addressing and routing data packets between devices over an IP network, using IP addresses.
- Transport layer - This layer provides end-to-end communication between devices and error control mechanisms, using protocols such as TCP and UDP.
- Application layer - This layer provides services to applications for network communication, such as HTTP for web browsing and SMTP for email.
Both models take the 1s and 0s from the physical or network interface layer, where the cables or Wi-Fi connect, to the Application Layer, where users interact with the data. The data traverses the network as packets, with headers or footers being added and removed accordingly as they get passed layer to layer. This helps route the data and ensures packets are not lost and remain together.
It's important to note that while the OSI model has seven layers and the TCP/IP model has four, they both describe similar functions and can be used together to understand network communication.
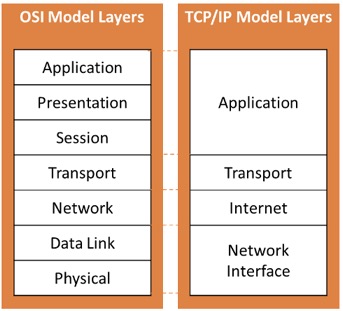
TCP/IP also includes a framework organising a set of communication protocols used in the Internet and similar computer networks according to functional criteria.
The foundational protocols are located at the transport layer:
- the Transmission Control Protocol (TCP), used for communication requiring no data to be lost during transmission, for example when exchanging data over the network and
- the User Datagram Protocol (UDP), used when no guaranteed delivery of data is required. This is used for example for live-streaming, where the loss of a few video-frame during the data transfer is acceptable.
In addition, the application layer offers a set of protocols used by most applications for providing user services or exchanging application data over the network connections established by the lower-level protocols.
Such protocols include:
- Hypertext Transfer Protocol (HTTP), used for exchanging webpage
- File Transfer Protocol (FTP) to exchange files,
- Simple Mail Transfer Protocol (SMTP) for email,
- Dynamic Host Configuration Protocol (DHCP) and more.
Cloud Solutions
Cloud computing has transformed the way businesses and individuals use technology. For a lot of organisations, cloud solutions provide access to powerful computers and software over the internet, without needing to own or manage the network and physical hardware. There are different ways to use cloud services, and various ways to set up cloud environments.
Cloud Service Models
- SaaS (Software as a Service): SaaS is the equivalent of renting an online software. Instead of buying and installing softwares on computers, users access them over the internet. Popular examples include Google Workspace (formerly G Suite), Microsoft 365, and cloud-based email services.
- PaaS (Platform as a Service): PaaS solutions offer organisations access to platforms for developing and deploying their own applications. In PaaS solutions, organisation do not have to manage the servers or the underlying infrastructure. They can focus on writing and running your software. Examples include Google App Engine and Heroku.
- IaaS (Infrastructure as a Service): IaaS is similar to renting the basic building blocks of computing. Organisations using IaaS get access to virtualised hardware, like servers, storage, and networking, which they can configure and manage. It's useful for businesses that need more control over their IT infrastructure. Examples include Amazon Web Services (AWS) and Microsoft Azure.
Responsibility | Owned (no cloud) | IaaS | PaaS | SaaS |
Data classification & accountability | Customer | Customer | Customer | Customer |
Client & end-point protection | Customer | Customer | Customer | Shared |
Identity and access management | Customer | Customer | Shared | Shared |
Application level controls | Customer | Customer | Shared | Vendor |
Network controls | Customer | Shared | Vendor | Vendor |
Host infrastructure | Customer | Shared | Vendor | Vendor |
Physical security | Customer | Vendor | Vendor | Vendor |
Cloud Deployment Models
Cloud solutions come in various deployment models that organisation can choose from:- Public Cloud: Public clouds are shared environments in the digital world. They are owned and operated by third-party cloud service providers and are accessible to anyone over the internet. Public clouds are cost-effective and scalable, making them suitable for a wide range of applications.
- Private Cloud: Private clouds are dedicated environments. Contrary to public cloud, private cloud have resources allocated to a specific customer. They are used exclusively by one organisation and can be hosted either on-premises or by a third-party provider. Private clouds offer greater control, security, and customisation but may be more expensive.
- Community Cloud: Community clouds are shared environments, but only among a specific group of organisations with shared interests or requirements. For example, community clouds dedicated to government institutions or education organisations offers cloud services shared only between such organisations. They are a good choice when multiple organisations need to collaborate while maintaining a certain level of data isolation and security.
- Hybrid Cloud: Hybrid clouds are a combination of different cloud deployment models. They allow data and applications to move between private and public clouds as needed. This flexibility is useful for businesses with changing or complex needs.
In summary, cloud computing comes in various flavours, from renting software and infrastructure to building your own applications. Organisations can choose the deployment model that best suits their requirements, whether it's a public, private, community, or hybrid cloud. The cloud has democratised technology, making powerful resources accessible to businesses and individuals of all sizes.
Conclusion
In the realm of technology, computer networks seamlessly connect our digital world. From the smallest Personal Area Networks (PANs) to the expansive Wide Area Networks (WANs), these networks are the backbone of our digital lives.We've explored the devices, IP addresses, DHCP, network ports, and critical network terms that define this landscape. Additionally, we've demystified network models and protocols that drive communication.
computer networks are the lifeblood of our interconnected world, transcending geographical boundaries and fostering collaboration on a global scale. They are the essence of modern communication, the foundation upon which the digital age is built.
Check your readiness with a Quiz: https://forms.office.com/r/iKsJbXYnLT
Disclamer: This article is not legal or regulatory advice. You should seek independent advice on your legal and regulatory obligations. The views and opinions expressed in this article are solely those of the author. These views and opinions do not necessarily represent those of HSBC or its staff. Artificial Intelligence Technology was used to read-proof this article.