🔐 Network Concepts

Get Certified in Cybersecurity - Part 4 of 6
🔐 Network Concepts
Discover the intricate world of computer networks. This article covers topics such as network types, essential devices, IP addresses, DHCP, network ports, and key network terms. It also explores the OSI and TCP/IP models, showcasing their role in network communication. Furthermore, the article touches upon cloud computing, highlighting different service and deployment models.
💡 Digital Identity and Authentication

Time to go through the concepts of Digital Identity and Authentication, and how they are generally implemented in IT environments to automate access to websites, services and applications.
While this article does not require any specific technical knowledge, it is not a trivial topic, and I have purposely tried to not oversimplify some of the concepts. I have done my best to keep it easy to read, but feel free to send some feedback if some parts are too complex and you would like further clarifications.
Microsoft Patches ‘Wormable’ Flaw in Windows XP, 7 and Windows 2003
💡 Creating a Secure Bring-Your-Own-Device Strategy

Corporate reality is that there is a growing interest from employees to use their personal devices for work. This can have a very positive impact on business – choosing which device is best for them and when, empowers workers and makes them more productive – but it also raises many security concerns for the enterprise – especially around access, confidentiality of information, compliance, security and privacy.
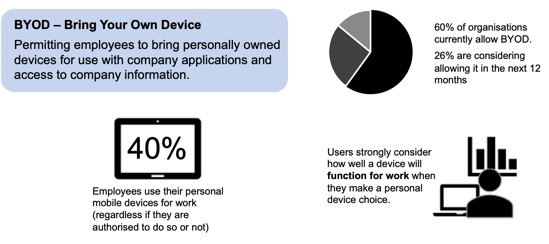
In order to define how employees will be able to interact with the corporate resources, the Bring-Your-Own-Device (BYOD) strategy is a critical part of your journey toward BYOD. It is there to define the capabilities your organisation offers to employees to use their personal laptops, smartphones or tablets for work.
To assist you in your journey, this article covers how to answer these questions and what are the options available for you in order to create a secure BYOD strategy.
Microsoft is privately testing 'Bali,' a way to give users control of data collected about them
💡 Understanding Meltdown and Spectre

As an executive or senior manager, what should I know and what should my company be doing about Meltdown and Spectre?
If you are not an IT Security specialist and you have been trying to understand what all the fuss is about - you are probably struggling to find articles that are not overly technical or too generic. Hopefully, this one will be answer your questions.