🔐 Security Operations
This article is part 6 (of 6) of a series to help you prepare for the ISC2 Certified in Cybersecurity (CC) certification.
The CC certification is a foundational certification that covers the core concepts and principles of cybersecurity. It is designed for anyone who wants to enter or progress in the cybersecurity field, regardless of their background or experience.
🎓 Become Certified in CyberSecurity series: https://www.jbbres.com/files/cc-2023.html
🎓 ISC2 Certified in Cybersecurity (CC): https://www.isc2.org/Certifications/CC
In an age where information is a valuable currency, ensuring its protection is paramount for any organisation. This article takes a deep dive into the realm of security operations, with a specific emphasis on data security. It provides comprehensive insights into the entire lifecycle of data, from its inception to its ultimate disposal. We'll examine the intricate process of data handling, explore the critical aspect of data classification, unravel the significance of robust logging mechanisms, and delve into the world of encryption and hash functions.
Furthermore, we'll discuss pivotal practices such as system hardening and configuration management, shedding light on how they can be leveraged to reduce vulnerabilities and enhance security within your organisation. Additionally, you'll gain a clear understanding of crafting security policies and procedures, covering areas like data handling, password management, acceptable use, BYOD policies, privacy, and change management.
One of the core pillars of security operations is security awareness training, which empowers individuals within your organisation to become the first line of defence against social engineering attacks and other cybersecurity threats. By the end of this article, you'll be well-equipped to navigate the intricate landscape of security operations, fortifying your organisation's defences and ensuring the safety of its most valuable asset: its data.
Data Security
Data security is a multifaceted process and discipline that serves as the backbone of an organisation's ability to protect its information assets. In this section we will look at the data handling process, delves into data sensitivity levels, and explores the importance of logging and encryption.Data Handling Process
The data life cycle is a conceptual framework that offers insights into how data evolves within an organisation. It encompasses everything from the moment data is first created until it's eventually retired. Picture it as a roadmap, guiding data through various stages: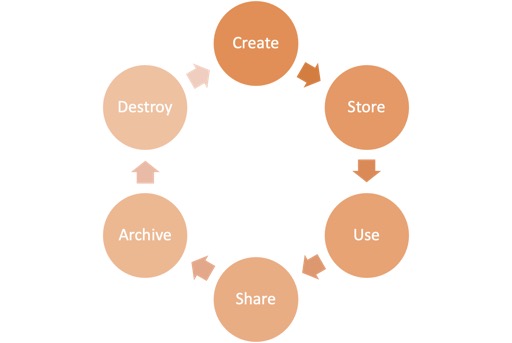
- Create: The journey begins with data creation. This stage involves generating or gathering new information. It also includes modifications to existing data.
- Store: Once created, data finds its first resting place. Organisations store data in one or more storage systems, which can be either on-premises or hosted by a cloud service provider.
- Use: Data comes alive in the "use" stage. This is where users and systems actively access, view, and process the information.
- Share: The sharing stage involves making data available to others through various mechanisms. It may include sharing links with customers, adjusting access controls to allow employees to view files, or similar actions.
- Archive: When data is no longer in active use but still holds value for historical or compliance purposes, it enters the archive stage. In this phase, data resides in long-term storage, not immediately accessible but retrievable if needed.
- Destroy: The final leg of the journey involves data destruction. When data is no longer needed, it must be securely disposed of to prevent any possibility of unauthorised access.
Data destruction is a critical aspect of data security. It must be executed meticulously to prevent scenarios where attackers obtain discarded paper or electronic media and reconstruct sensitive data.
There are three essential activities for sanitising electronic media:
- Clearing: This involves overwriting sensitive data with new data, rendering the old data unrecoverable. It's effective against most casual analysis.
- Purging (or Wiping): Purging is similar to clearing but uses more advanced techniques, including cryptographic functions and degaussing (applying strong magnetic fields) to obscure data on disks.
- Destroying: The ultimate form of data sanitisation, destruction involves rendering media irrecoverable. Methods include shredding, pulverising, melting, incinerating, or otherwise obliterating the media. However, this method precludes media reuse.
- Shredding: Crosscut shredders cut paper into tiny pieces, making reassembly nearly impossible.
- Pulping: Chemical processes remove ink from paper, converting it into pulp for recycling into new paper products.
- Incineration: While less environmentally friendly due to carbon emissions, incineration is an option for paper record disposal.
While the data life cycle's stages are not always followed sequentially, and not every piece of data undergoes all stages, it serves as a valuable model for comprehending the various phases of data existence. Understanding and implementing these stages and secure data destruction practices are fundamental components of robust data security.
Data Classification
Data classification is a foundational practice in data security. It helps users comprehend the security requirements associated with handling different types of data. Classification policies articulate the security levels of information within an organisation and provide a framework for assigning data to specific classification levels. These classifications dictate the appropriate storage, handling, and access requirements for categorised data.Organisations base classifications on two key factors:
- Sensitivity of Information: This refers to the degree of confidentiality, integrity, and availability required to safeguard the data. Sensitivity levels can vary widely based on the nature of the information.
- Criticality to the Organisation: The importance of data to an organisation influences its classification. Data that is critical to an organisation's core functions may receive higher levels of protection.
Common Data Sensitivity Levels
Organisations employ various classification schemes, but they typically group information into high, medium, and low sensitivity levels, with distinctions between public and private information. Here are common sensitivity levels:- Highly Restricted: Data with this sensitivity label is of the utmost importance. Compromising such data could potentially threaten the organisation's very existence. The consequences may include substantial loss of life, injury, property damage, and ensuing litigation and claims. Example of data that would usually be considered as Highly Restricted: customer personal data, password, undisclosed strategic plans.
- Moderately Restricted: Data classified as moderately restricted is valuable and sensitive. Its compromise might result in the loss of temporary competitive advantage, revenue, or disruption of planned investments or activities. Example of moderately restricted data: contracts with providers, minutes of governance meetings…
- Low Sensitivity (sometimes called "Internal Use Only"): Data with this label is of lower sensitivity. Compromise may lead to minor disruptions, delays, or impacts, but it does not pose a severe threat to the organisation: Example of Low sensitivity data: company policies, office supplies inventory…
- Unrestricted Public Data: This category includes data that is already publicly accessible. No harm can arise from further dissemination or disclosure of such data. Example of public data: press releases, job posting…
When organisations classify information, they should also define labelling requirements. These labels provide consistent markings for sensitive information, ensuring that users can consistently recognise and handle it appropriately. This consistency is vital for maintaining data security. For example, a company might mandate for the sensitivity level to be prominently displayed on a document when printed.
Logging
Effective data security includes robust logging mechanisms that facilitate monitoring and analysis of security events.Logs provide a wealth of information for security professionals. Properly configured logging systems can help organisations achieve three critical objectives:
- Accountability (Identity Attribution): Logs help determine who or what caused a specific event, whether it's attributed to a person, a computer's IP address, or a geographic location.
- Traceability: Logs allow security teams to trace related events and incidents, aiding in incident investigation and response.
- Auditability: Logging provides clear documentation of actions, ensuring transparency and compliance with security policies and regulations.
A log anomaly is an event that deviates from the expected behaviour of a system. It could indicate a security breach, a malfunctioning device, or an error in the configuration of the system. For example, a motion detector that triggers an alarm when no one is supposed to be in the area could be considered a log anomaly.
Log consolidation is the process of aggregating logs from different sources into a central repository. This can help simplify log management, improve visibility, and facilitate analysis. For example, a security operations centre (SOC) might use log consolidation to collect logs from all the security devices in a facility.
Log retention refers to the duration for which logs are stored. This is usually determined by legal, regulatory, or business requirements. Logs may need to be retained for several months or even years, depending on the nature of the data and the applicable laws and regulations. Log retention policies should be carefully designed to balance the need for data retention with the cost of storage and the potential risk of data breaches.
Logs are generated and monitored both from an ingress perspective (what is trying to come inside the organisation network) and from an egress perspective (what is trying to leave the network)
Ingress monitoring tools are instrumental in tracking activities entering an organisation's network. They generate valuable logs that can be analysed to detect and respond to security threats. Here are some common ingress monitoring tools:
- Firewalls: Firewalls serve as the gatekeepers of network traffic, filtering incoming and outgoing data packets. Firewall logs provide insights into blocked and allowed traffic, aiding in the identification of potential threats.
- Gateways: Gateway devices control the flow of data between networks, and their logs help organisations monitor incoming connections and network activities.
- Remote Authentication Servers: These servers log authentication attempts, making it possible to detect unauthorised access and intrusion attempts.
- IDS/IPS Tools (Intrusion Detection/Prevention Systems): IDS/IPS tools monitor network traffic patterns for signs of malicious activity. Their logs are crucial for identifying and responding to potential breaches.
- Anti-malware Solutions: Anti-malware software generates logs when it detects and mitigates threats. These logs provide information about malware activities and help security teams respond swiftly.
Egress monitoring focuses on tracking data leaving the organisation's network. This entails monitoring various data types and activities through Data Loss Protection (DLP) solutions. Monitored data includes:
- Email (Content and Attachments): Monitoring outbound email traffic helps prevent data leakage and unauthorised sharing of sensitive information.
- Copy to Portable Media: Detecting data copied to USB drives or external storage devices helps prevent data exfiltration.
- File Transfer Protocol (FTP): Monitoring FTP traffic is essential to identify file transfers, which may include sensitive data.
- Posting to Web Pages/Websites: Tracking data posted to web pages or websites ensures that sensitive information is not publicly exposed or disclosed.
- Applications/Application Programming Interfaces (APIs): Monitoring data leaving through applications or APIs is crucial for preventing data breaches, especially in cloud-based environments.
Security Information and Event Management (SIEM)
However, the sheer volume of log entries generated daily can be overwhelming for security professionals. To address this challenge, organisations often employ Security Information and Event Management (SIEM) systems, usually powered with robust artificial intelligence capabilities..SIEM systems play a pivotal role in security log analysis. They serve two main functions:
- Centralised Collection: SIEM systems act as secure collection points for log entries from various systems, network devices, and applications. This ensures the secure storage of log data.
- Correlation: SIEM systems employ Artificial Intelligence and log correlation techniques to detect patterns of potential malicious activity. By analysing logs from across the organisation, SIEMs can piece together the puzzle of security incidents.
For example, an intrusion detection system may detect a unique attack signature in inbound network traffic. The SIEM can correlate this with other information, such as an unfriendly country's inbound connection to a web server, suspicious SQL injection queries, anomalous database queries, and unusual data flow patterns. This comprehensive view allows security professionals to identify patterns of suspicious activity that might go unnoticed when viewed in isolation.
Logs are a critical component of data security, providing the means to monitor, investigate, and respond to security incidents. SIEM systems enhance log analysis by centralising log collection and applying AI-driven log correlation to detect complex security threats across the organisation.
Encryption
Encryption is a cornerstone of data security, serving as one of the most potent controls to protect the confidentiality of information. It employs complex mathematical algorithms to transform data into an unreadable format, rendering it accessible only to authorised users. While the underlying math is intricate, it's essential to grasp the basics of what encryption accomplishes and how it fortifies an organisation's security posture.The encryption process follow a few key steps:
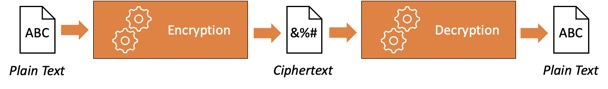
- Plain Text Data: Encryption begins with plain text information, which is the original, readable form of the data.
- Encryption Algorithm: An encryption algorithm, coupled with an encryption key, is used to encode the data. The algorithm is a mathematical formula, and the key functions as a password to access the data.
- Ciphertext: The outcome of the encryption process is known as ciphertext. Ciphertext is entirely incomprehensible to anyone who tries to examine it, appearing as gibberish.
- Decryption: To revert ciphertext to its original form, authorised users employ a decryption algorithm and the decryption key. Without the correct decryption key, it is impossible to decrypt the data, ensuring data security.
Encryption serves two primary environments:
- Data at Rest: This pertains to stored data, whether it's individual files, entire disks, or mobile device content. Unauthorised access to encrypted data is futile without the corresponding decryption key.
- Data in Transit: Data in transit is information traversing a network. Encryption protects data during transmission, ensuring that eavesdroppers cannot intercept or decipher sensitive information. For example, the use of HTTPS encryption secures web connections.
Encryption algorithms fall into two major categories: symmetric and asymmetric encryption.
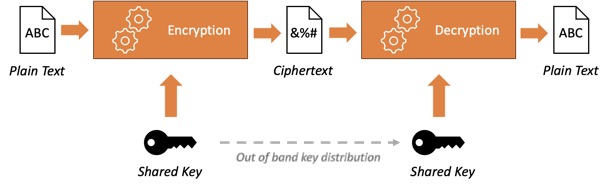
Symmetric Encryption, also known as shared secret encryption, employs the same key for both encryption and decryption. If two parties share a secret key, they can encrypt and decrypt messages privately. However, when multiple parties need to communicate securely, the key management complexity increases significantly.
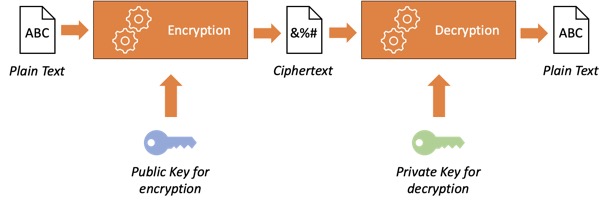
Asymmetric Encryption or public-key encryption, employs different keys for encryption and decryption. It utilises a key pair—a public key, which can be freely shared, and a private key, which must remain secret. Messages encrypted with the public key can only be decrypted using the corresponding private key. Asymmetric encryption simplifies key distribution in multi-party communication.
Hash Functions
Hash functions play a pivotal role in data security, particularly in creating digital signatures and certificates. A hash function is defined as a one-way function that transforms variable-length input into a unique, fixed-length output.- One-Way Function: Hash functions are irreversible, meaning you cannot reverse the process to retrieve the original data from its hash value.
- Variable-Length to Fixed-Length: Hash functions maintain a consistent output length regardless of the input length.
- Unique Output: For a hash function to be effective, it must produce unique hash values for different inputs, preventing collisions where two different inputs result in the same hash value.
Weak hash functions can be susceptible to attacks known as birthday attacks. A birthday attack is a cryptographic exploit that takes advantage of the birthday paradox, which states that in a set of just 23 randomly chosen people, there's a 50% chance that two of them share the same birthday. In the context of cryptography, this paradox becomes a vulnerability when dealing with hash functions. A birthday attack targets the collision resistance of hash functions (the fact that it produces a unique hash value for each different input), attempting to find two inputs that produce the same hash value.
Despite the large output space of hash functions, due to the nature of the birthday paradox, it's statistically feasible for an attacker to generate two different inputs that produce the same hash, compromising the integrity and security of the hash function. This attack highlights the importance of robust cryptographic hash functions that resist collision attacks and the need for longer hash lengths to mitigate this vulnerability.
Encryption and hash functions are fundamental to data security, ensuring confidentiality, integrity, and authenticity. Understanding the principles behind these cryptographic tools is crucial for protecting sensitive information in various environments and scenarios.
System Hardening
System hardening is a critical cybersecurity practice aimed at reducing the attack surface of an organisation's infrastructure. It involves configuring systems, applications, and network components to minimise vulnerabilities and enhance security. System hardening can be applied at multiple levels:- Operating Systems: Securing the operating system involves disabling unnecessary services and features, implementing access controls, applying security patches regularly, and configuring user permissions and passwords to ensure only authorized users can access the system. This apply to both servers and workstations.
- Web Servers: Web servers are prime targets for cyberattacks. To harden them, administrators should disable unused modules, enable security features like SSL/TLS encryption, regularly update server software, and employ web application firewalls (WAFs) to filter and protect against malicious traffic.
- Application Servers: Application servers, which host and run web applications, must also be hardened. This includes configuring application security settings, patching vulnerabilities in the applications themselves, changing default passwords and implementing access controls to restrict unauthorized access to sensitive data.
- Applications: Secure coding practices are crucial for application hardening. Developers should follow security best practices, conduct code reviews, and regularly update applications to fix known vulnerabilities. This apply to both servers and workstations.
Configuration Management
Configuration management ensures that systems and applications are in a known and trusted state. It involves the following key steps:- Identification: Identify all system components and their configurations, including hardware, software, and network resources. This forms the basis for managing changes.
- Baseline: Establish a baseline configuration for each system, which represents a known and secure state. Any changes made to the system should be compared against this baseline to detect unauthorised alterations.
- Change Control: Implement a structured process for requesting, approving, and validating changes to systems and applications. This helps prevent unauthorised or undocumented changes that could introduce security risks.
- Verification and Audit: Regularly verify and audit configurations to ensure compliance with security policies and standards. Automated tools and Security testing, including penetration testing and vulnerability scanning can help detect discrepancies and non-compliance.
System hardening and configuration management are crucial components of a robust cybersecurity strategy. They help organisations proactively reduce vulnerabilities, protect against cyber threats, and maintain the integrity and security of their IT environments. By following best practices in these areas, organisations can significantly enhance their overall cybersecurity posture.
Best Practice Security Policies
Effective cybersecurity operations also rely on comprehensive security policies. In this section, we'll explore the key components of some key security policies that can help organisations bolster their security posture.Data Handling Policy
The data handling policy ensures that employees use data in a manner that aligns with organisational objectives, legal requirements, and ethical standards. It provides a framework managing data:- Classify: Categorise data based on its sensitivity and value to the organisation.
- Label: Apply appropriate labels or markings to data to indicate its sensitivity and handling requirements.
- Store: Determine secure storage methods for different data classifications, whether it's in encrypted databases or locked filing cabinets.
- Encrypt: Implement encryption to protect data in transit and at rest, especially for highly sensitive information.
- Backup: Regularly back up data to prevent loss in case of hardware failure or data corruption.
- Destroy: Establish secure procedures for the destruction of data that is no longer needed, ensuring it cannot be recovered.
Password Policy
The Password policy lays down rules and guidelines for creating, managing, and protecting passwords to prevent unauthorised access. It provides guidelines of various aspects of password management:- Password Creation: Establish rules for password length, complexity, and avoidance of easily guessable patterns. Encourage the use of longer passphrases. For instance, the policy may demand a mix of uppercase and lowercase letters, digits, and special characters.
- Password Aging: Define password change schedules for users and system-level passwords, preventing password reuse. For example, a policy might set a password expiration period of 180 days, prompting users to change their passwords every six months. However, it's worth noting that modern security practices are shifting away from mandatory password changes, opting instead for change only when there's a potential compromise.
- Password Protection: Strictly prohibit password sharing, electronic transmission, or written documentation. It emphasises the importance of keeping passwords confidential.
Acceptable Use Policy (AUP)
The AUP defines how employees and users should interact with organisational resources, encompassing hardware, software, and data. It specifies aspects such as:- Data Access: Specify who can access data and under what conditions.
- System Access: Define rules for accessing and using organisational systems, networks, and resources.
- Data Disclosure: Outline procedures for sharing and disclosing data, both within and outside the organisation.
- Passwords: Reinforce password-related rules and security measures within the AUP.
- Data Retention: Determine data retention, archiving, and deletion policies.
- Internet Usage: Govern employees' responsible and secure internet usage during work hours.
- Company Device Usage: Detail the usage of company-owned devices, including security practices and compliance.
Bring Your Own Device (BYOD) Policy
The BYOD policy addresses the use of personal devices for work-related purposes while ensuring security and privacy. It sets guidelines for securing personal devices used for work.The types of devices covered by a BYOD policy includes devices such as mobile phones, tablets, laptops, smartwatches, Bluetooth devices…
Privacy Policy
The privacy policy safeguards individuals' privacy by outlining how personal information is collected, stored, and used. It focuses on the protection of Personally Identifiable Information (PII), electronic Protected Health Information (ePHI), and sensitive financial data such as bank details and credit card information..Change Management Policy
The change management policy provides a structured approach to managing changes within an organisation, ensuring that changes are well-planned and controlled. It encompasses deciding to change, making the change, and confirming the change's successful implementation.These best practice security policies provide a structured and organised approach to securing an organisation's data and resources. By implementing these policies, organisations mitigate risks, protect sensitive information, ensure user compliance, and smoothly manage changes, ultimately fostering a secure and compliant environment.
Security Awareness Training
Social Engineering
Information security is not solely about defending against digital threats. Some of the most insidious risks come from human threats, particularly social engineering attacks. These attacks leverage psychological tactics to manipulate individuals into performing actions or revealing sensitive information, ultimately compromising an organisation's security.Social engineering attacks often employ familiar tactics to manipulate individuals:
- Authority: Individuals tend to trust and defer to those who project an aura of authority, whether through professional attire or a commanding demeanour. This trust has been validated in psychological experiments and real-world scenarios.
- Intimidation: Some attackers resort to intimidation tactics, pressuring targets with threats or inducing fear. For example, masquerading as an administrative assistant and demanding immediate action can effectively coerce compliance.
- Consensus: In situations of uncertainty, people often mimic the behaviour of others, leading to herd mentality. Attackers exploit this tendency, particularly in chaotic or emergency scenarios, to sway individuals towards their objectives.
- Scarcity: By creating a perception of urgency, attackers persuade individuals that quick action is imperative to avoid missed opportunities. This tactic is frequently used in limited-time offers or situations requiring rapid decisions.
- Urgency: Attackers leverage urgency to force swift decisions, implying severe consequences for any delay. This strategy is commonly observed in tech support scams and repair-related scenarios.
- Familiarity: Establishing rapport and trust by employing flattery or fabricating personal connections enables attackers to gain the confidence of their targets. People are more inclined to comply with requests from those they like. Tailgating (entering unauthorised a secured area by closely following an authorised person through a controlled access point) usually leverage familiarity, as employees would believe they are letting an authorised colleague into a restricted area.
- Curiosity: leveraging human curiosity or desire for gain to manipulate victims. An example is baiting, where malicious actors offer enticing items (such as an abandoned USB key), enticing individuals into taking actions that compromise security (putting the USB key in their computer), often leading to malware infection or data theft.
Defending against social engineering attacks primarily relies on user education. Every member of an organisation should be aware of these tactics and vigilant against outsiders using authority, intimidation, consensus, scarcity, urgency, or familiarity to manipulate them or their colleagues.
Impersonation Attacks
Spam, often seen as unsolicited commercial email (UCE), is a well-known nuisance. It encompasses unwanted messages sent for various purposes, including marketing and identity fraud. While spam is often punishable by law, prosecution can be challenging due to anonymity.- Phishing: A subset of spam, phishing messages aim to extract sensitive information. Attackers use tactics like warning users of limited email space to trick them into revealing login credentials, leading to account compromise. Phishing is often a prelude to more extensive attacks.
- Spear Phishing: Highly targeted, spear phishing attacks focus on specific groups, using business jargon and leaders' names for legitimacy. These attacks often succeed due to their authoritative tone.
- Invoice Scams: Attackers send fake invoices to accounts receivable departments, hoping they'll be paid inadvertently.
- Whaling: Targeting senior executives, whaling attacks aim to exploit their authority and influence. Attackers might send fake legal documents to infect systems or gain access.
- Pharming: These attacks use phishing messages and fake websites, often employing typosquatting to create convincing URLs. Users unknowingly provide credentials to attackers.
- Vishing: Voice phishing or vishing attacks use social engineering tactics over phone calls to extract sensitive information or deceive users into installing malicious software.
- Smishing: Similar to email phishing, smishing targets users via instant messaging services, using SMS or iMessage. Spoofing is commonly employed to impersonate others.
Attackers employ various tactics, from basic to sophisticated, in their impersonation attempts. It's crucial to understand that not all attempts need to succeed. A single victim can be enough for an attack to achieve its goal. Therefore, education and awareness are vital defences against social engineering attacks.
Security Awareness Training
Security hinges on individuals' behaviour, making security awareness training programs a critical component of any organisation's defence strategy. These programs consist of two main elements:- Security Training: This component imparts detailed knowledge to users about protecting an organisation's security. Training methods vary, from classroom instruction to online courses or integrating security content into existing programs like new employee orientations.
- Security Awareness: Unlike training, awareness doesn't require users to dedicate significant time to learn new material. Instead, it uses various techniques like posters, videos, emails, and reminders to reinforce security principles previously learned.
Various methods can be employed to deliver security training, including traditional classes, online courses, or vendor-provided training modules. The key is to cater to different learning styles and tailor training to individual roles within the organisation. For instance, employees handling sensitive data should receive training specific to their responsibilities.
When determining the frequency of training, organisations must strike a balance between reinforcing security and not overburdening employees. Initial training upon joining the organisation or assuming new responsibilities can be followed by annual refresher training. Throughout the year, ongoing awareness efforts keep security at the forefront of employees' minds.
Continual review and updating of training materials are essential to ensure their relevance in a dynamic security landscape. Changes in the security landscape and the organisation's business may necessitate updates to keep training content fresh and pertinent.
Security awareness training is a crucial defence against social engineering attacks, reinforcing the human element of security. By educating and reminding employees of their responsibilities and the evolving threat landscape, organisations can foster a culture of security and resilience against cyber threats.
Conclusion
In an era defined by the relentless advance of technology, the security of information is a matter of paramount importance. The protection of individuals and organisations data requires a multifaceted approach that encompasses every facet of operations.From the inception of data to its eventual destruction, understanding the intricate data handling process is crucial. Data classification provides the bedrock upon which security decisions are made, allowing you to tailor your protection measures to the specific needs of each category of data.
Robust logging mechanisms serve as the sentinel guardians of your digital realm, providing invaluable information for monitoring and responding to security events. Encryption and hash functions ensures the confidentiality, integrity, and authenticity of information.
System hardening and configuration management fortifies technology against potential vulnerabilities and maintaining the integrity of your systems.
The creation and implementation of sound security policies lay down the rules of engagement, ensuring that every employee understands their role in protecting sensitive data. These policies encompass everything from data handling and password management to acceptable use and change management.
In the realm of social engineering attacks, awareness is every organisation’s greatest ally. Through security awareness training, employees become the first line of defense against threats that target the human element of your organisation.
Organisation's security is an ongoing process. Stay vigilant, adapt to the evolving threat landscape, and prioritise a culture of security. By doing so, you'll safeguard your organisation's future in the digital age and fortify its resilience against cyber threats. Your commitment to security is an investment that will pay dividends in the protection of your most valuable assets, ensuring a safer and more secure future for your organisation.
Check your readiness with a Quiz: https://forms.office.com/r/RCinSMjTY8
Disclamer: This article is not legal or regulatory advice. You should seek independent advice on your legal and regulatory obligations. The views and opinions expressed in this article are solely those of the author. These views and opinions do not necessarily represent those of HSBC or its staff. Artificial Intelligence Technology was used to read-proof this article.