DevOps role @ Xinja
You’ll work with software engineers and security experts to ensure that the right practices are in place and to take the security lead on automating the path to production to enable deployment of changes with no manual intervention and in a highly secure manner.
We run a small, crack team of DevOps engineers to help us to build out a world class continuous integration and delivery pipeline for the Xinja Banking Platform as we continue to scale at pace. You will ensure security standards are upheld and secure coding practices maintained.
If you think this is something for you, contact me or visit Xinja career website for more information.
💡 What is Identity Theft? (a beginner guide)

With Christmas coming fast, it is a great time to remember identity crime is a critical threat to the everyone. A short beginner guide on how to protect yourself against identity theft and what to do if your identity get stollen.
Read More…Is Australia struggling from a bout of breach fatigue
Unto the breach: let’s face up to data security
Cyber Attack Conference Sydney 2019
Let's. Go.
Read more at https://www.xinja.com.au/news/2019/xinja-gets-full-banking-licence/

Xinja is #5 top startups to work for now!
Australian banks face secret penetration tests
Read more at http://bit.ly/2lyNQT4
What will future jobs look like?
Super Risk Symposium - Melbourne 14/08
It was a great session, on the impact of the new CPS 234 regulation, thanks to Rob Pickering who facilitated the debate and to Joss Howard and Matt O'Keefe for their great insights.

Security Designer @ Xinja
If you think this is something for you, contact me or visit Xinja career website for more information.
Info Sec GRC Manager @ Xinja
This is a key role for the organisation: You will manage the information risk and security governance, focussing on raising standards and awareness, as well as providing assurance and monitoring compliance with policies and standards.
If you think this is something for you, contact me or visit Xinja career website for more information.
More openings coming soon… 😉
DevSecOps role @ Xinja
You’ll work with software engineers and security experts to ensure that the right practices are in place and to take the security lead on automating the path to production to enable deployment of changes with no manual intervention and in a highly secure manner.
We run a small, crack team of DevOps engineers to help us to build out a world class continuous integration and delivery pipeline for the Xinja Banking Platform as we continue to scale at pace. You will ensure security standards are upheld and secure coding practices maintained.
You should know that we do things a little differently at Xinja. You won’t be micromanaged and will have the flexibility to choose the tools you need to get your work done. Along with the team you work with, you’ll be given autonomy on how you design and build DevSecOps processes as long as it stays within the guidance of the Xinja Software Development Lifecycle and Information Security Management System. You should be comfortable with pushing new tools and processes and challenging the norms of secure software development and deployment.
If you think this is something for you, contact me or visit Xinja career website for more information.
More openings coming soon… 😉
Security Analyst role @ Xinja
If you think this is something for you, contact me or visit Xinja career website for more information.
More openings coming soon… 😉
Your inbox is spying on you
"When we built [our company], we focused only on the needs of our customers. We did not consider potential bad actors." 😧
Read more: https://lnkd.in/gRWsFKW
Super Risk Symposium - Melbourne 14/08
Information security is all about risk management. With APRA’s CPS 234 framework now live, how do funds need to be secured and why? What is an acceptable risk? And what is the lasting impact if valuable data is compromised, exposed or unavailable?
This session will explore how funds are demonstrating compliance with the new prudential standard and the strategies being used in safeguarding systems against information security threats.
[Update] Info and tickets at https://bit.ly/2GGHp8v
RBA details disaster recovery efforts
In August 2018, the Reserve Bank of Australia faced a disruption to the power supplying the data centre at one of its site (primary and backup) due to a vendor error. Then multiple factors, from super-high security to plain bad luck, made the recovery difficult, and the bank did not manage to recover within their recovery time objective (RTO).
This article details the extent of the events. It is a very interesting story for everybody interested in continuity and disaster recovery. And also kudo to the RBA for the retrospective analysis of their own efforts, their honesty about what did not go as well as planned, and their transparency in sharing their findings with the rest of the industry.
Is your cybersecurity training reaching the right people?
Want to Take Better Notes? Ditch the Laptop for a Pen and Paper
I personally always struggled taking notes on a computer and have been a fierce user of notebooks (especially since I discovered reusable ones). Well now I will have an even better excuse to continue doing so 😄
💡 Conference Transcript: Building an Information Security Policy Framework

Following my presentation on Building an Information Security Policy Framework at the "Implementing CPS 234" conference held in Sydney in May 2019, I received many requests to publish a transcript. Thank you all for your interest and for the large amount of feedback you shared with me. As promised, here is an augmented transcript of my presentation.
It covers an overview of what a Policy Framework is, and why it is an essential part of any Information Security program; the various existing frameworks used across the industry, their strengths and limitations; a methodology to create a flexible framework, supported by a risk assessment and a strong understanding of the assets owned by the institution and the threats they are exposed to; and an approach to define an adequate control set and how to prioritise its implementation.
Microsoft Patches ‘Wormable’ Flaw in Windows XP, 7 and Windows 2003
Tapping into the power of humble narcissism
First State Super integrates advice, overhauls leadership
First State Super has fully integrated its financial advice business, StatePlus.
In a move aimed at making financial advice accessible for all its members, the $70 billion fund has brought its financial advice business StatePlus in-house. Read more at http://bit.ly/2XqxFFu
💡 Creating a Secure Bring-Your-Own-Device Strategy

Corporate reality is that there is a growing interest from employees to use their personal devices for work. This can have a very positive impact on business – choosing which device is best for them and when, empowers workers and makes them more productive – but it also raises many security concerns for the enterprise – especially around access, confidentiality of information, compliance, security and privacy.
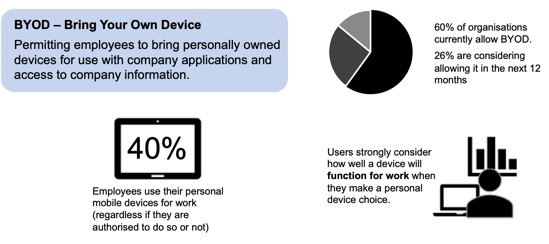
In order to define how employees will be able to interact with the corporate resources, the Bring-Your-Own-Device (BYOD) strategy is a critical part of your journey toward BYOD. It is there to define the capabilities your organisation offers to employees to use their personal laptops, smartphones or tablets for work.
To assist you in your journey, this article covers how to answer these questions and what are the options available for you in order to create a secure BYOD strategy.
How to keep human bias out of AI
Here is a great talk from Kriti Sharma @ TED on how to keep human bias out of AI.
"Implementing CPS 234" conference
I will be talking on how to build an information security policy framework that is agile to changing threats.
💡 Public Cloud ☁️ - Australia and New Zealand Regulatory Landscapes

More than ever, financial institutions in Australia and New Zealand are moving toward public cloud computing as a way to benefit from easy to use, flexible, cost effective and reliable infrastructures and services. Despite its substantial benefits, cloud computing also creates a complex new environment for financial institutions to navigate. Regulators in Australia and New Zealand are evolving their requirements and guidelines. It results in a growing expectation that financial institutions have a robust governance over their outsourcing process and ensure a high level of oversight of their cloud service providers. This article discusses the regulatory requirements around usage of Cloud Services in Australia and New Zealand and how to satisfy them.
Read More…