Geopolitics Is Now a Technology Risk

Geopolitics has become a direct and material technology risk, and it now firmly belongs on the CISO’s agenda. 🌐 Trade disputes, sanctions, cyber espionage, and digital sovereignty are reshaping where data lives, who can access it, and how resilient our platforms really are.
Our dependence on globally distributed supply chains and a small number of predominantly US-based ☁️ cloud providers has concentrated high‑value data and critical services in a few strategic locations. In a heightened geopolitical environment, cloud data centres are now strategic infrastructure, and disruptions—malicious or not—can quickly become systemic business events.
In this article, I explore why technology is uniquely exposed to geopolitical shocks and what CISOs and technology leaders should be doing now to factor geopolitics into cloud, availability, and resilience planning.
💡 You Can’t Secure What You Can’t See: The Case for SBOMs

Modern software is assembled from countless third‑party and open‑source components. And if you can’t see them, you can’t secure them. 🔎🔐
This article explains why SBOMs (Software Bills of Materials) are becoming essential for managing supply‑chain risk, strengthening incident response, and meeting rising security and compliance expectations.
If you want faster visibility, better control, and fewer surprises in your software stack, this one’s for you.
💡Agentic AI's Identity Crisis

Agentic AI — autonomous 🤖 agents that can perceive, decide, and act — are entering business workflows fast. But as these non-human “digital workers” multiply, identity has become the hidden challenge.
Most enterprises haven’t extended authentication and access controls to these agents, creating ungoverned digital personas operating at machine speed: a serious security risk.
This article explores why identity is the new frontier of AI security, and how cybersecurity leaders can govern agentic AI safely through strong authentication, lifecycle management, and accountability.
💡 Quantum Computing and the Future of Encryption

Quantum computing promises breakthroughs in science, medicine, and technology — but it also poses one of the biggest challenges yet to our digital security.
This article explores why organisations should be preparing now for a post-quantum world — not out of panic, but prudence.
Because when the flood comes, you don’t want to be halfway across the bridge.
- 🔒 What happens when quantum computers can break today’s encryption?
- 🧭 Why “harvest now, decrypt later” makes this a present-day risk?
- 🛠️ And how can organisations start planning for the transition?
💡 Cyber Risk Monitoring

Cyber risk monitoring isn’t just a technical task—it’s the backbone of staying resilient in a fast-changing digital landscape. From protecting critical assets to navigating strict security frameworks like NIST or ISO/IEC 27001, it’s about building a shield that adapts as threats evolve.
Discover how tailored strategies, real-time insights, and cutting-edge tools like AI and big data analytics are redefining risk management. Learn why collaboration, workforce upskilling, and flexible frameworks are the keys to thriving in this era of complex challenges.
💡 Risk Management in Technology

Learn about the importance of risk management in technology, particularly in mitigating cybersecurity threats, preventing system outages, and building trust with stakeholders.
This article covers the risk management process, including risk identification, assessment, treatment, and monitoring, as well as the significance of controls in information security.
Additionally, it introduces the concept of a quantitative risk model for assessing and managing risks using numerical data and metrics to enhance control effectiveness and resilience against cybersecurity threats.
🔐 Security Operations

Get Certified in Cybersecurity - Part 6 of 6
🔐 Security Operations
Learn key elements of data security, including data handling, classification, logging, encryption, system hardening, configuration management, security policies, and social engineering defence through security awareness training.
🔐 Network Security

Get Certified in Cybersecurity - Part 5 of 6
🔐 Network Security
Delves into common threats and best practices for securing computer networks. It explores the array of network threats, from malware and ransomware to insider threats, and understand how network professionals mitigate these risks.
🔐 Network Concepts

Get Certified in Cybersecurity - Part 4 of 6
🔐 Network Concepts
Discover the intricate world of computer networks. This article covers topics such as network types, essential devices, IP addresses, DHCP, network ports, and key network terms. It also explores the OSI and TCP/IP models, showcasing their role in network communication. Furthermore, the article touches upon cloud computing, highlighting different service and deployment models.
🔐 Access Management

Get Certified in Cybersecurity - Part 3 of 6
🔐 Access Control
Delves into the importance of access control, covering concepts encompassing defence in depth, least privilege, segregation of duty, two-person integrity, passwords, multi-factor authentication, privileged access management, account provisioning, log management, physical access control, biometric access control, and logical access control.
🔐 Incident Response, Business Continuity and Disaster Recovery

Get Certified in Cybersecurity - Part 2 of 6
🔐 Incident Response, Business Continuity and Disaster Recovery
Explore the crucial aspects of cybersecurity incident response, business continuity, and disaster recover. We will talk about the importance of incident response plans, business impact analysis, recovery strategies, and crisis management in ensuring the resilience and continuity of organisations in the face of cyber threats and disruptive events.
🔐 Key Security Principles

Get Certified in Cybersecurity - Part 1 of 6
🔐 Key Security Principles
Discover the essentials of safeguarding sensitive data and protecting against cyber threats. From the CIA Triad to Risk Management and Privacy, this article breaks down key principles in an accessible way.
💡 Certified in CyberSecurity - Your Journey to Certification

🚀 Unlock your path to a career in cybersecurity with the ISC2 Certified in Cybersecurity (CC)!
As part of Cyber Awareness Month 2023, I'll be sharing a series of articles throughout October covering the all the knowledge needed to prepare for the ISC2 Certified in Cybersecurity (CC).
Ideal for IT professionals, career changers, executives, and recent grads, this entry-level certification offers free exam and online training for a limited time, making it more accessible than ever.
Find out more about the ISC2 CC Certification. Your cybersecurity journey starts here!
💡 Ensuring CyberSecurity in Vendor Management

As our interconnected world amplifies cyber risks in the supply chain, the indispensable role of vendor managers in protecting valuable assets cannot be overlooked. With their unique insights and strategic position, they are instrumental in identifying and mitigating potential vulnerabilities.
This article provides vendor managers with invaluable guidance on elevating their role in safeguarding the supply chain. From selecting secure vendors to establishing robust contractual agreements, they will find actionable steps to fortify their organisation's cybersecurity posture.
💡 ChatGPT and the future of CyberSecurity

If you have been using ChatGPT, you probably feel now that nothing will never be the same. It is the same feeling you had when you used the internet for the first time, when you touched your first iPhone. There will be a before and an after Artificial Intelligence, and the tipping point is now.
It is hard to predict what a world supported by AI will look like. Some think it will be a scary place, some see a lot of exciting opportunities. But regardless what your views are, there is no denying that the cybersecurity industry will be - and already is - particularly affected. Tools like ChatGPT are a new set of capabilities, with both new opportunities and new challenges for security professionals.
💡 Your Home under Cyber Attack

As Cyber Awareness Month is coming to an end and Halloween is almost upon us, I thought it would be a great time to share a few real cyber-horror stories, and how to protect yourself from them.
💡 The CIA Triad (explained to non-security people)

A short article explaining what the CIA Triad is, or how Security is focusing on key concepts: Confidentiality, Integrity and Availability.
It's not always easy for non-security people to understand the challenges and endless efforts spent by security staff, so hopefully you will now have a better idea of why, and how, we do it.
💡 Vulnerability Management (explained to non-security people)

A short article explaining what is Vulnerability Management - one of the key areas of Information Security.
It's not always easy for non-security people to understand the challenges and endless efforts spent by security staff trying to remediate vulnerabilities, so hopefully you will now have a better idea of why, and how, we do it
💡 Defence in Depth

"Defence in depth", sometime also called “layering” is a central concept in information security. It relates to the idea that security components should be designed so they provide redundancy in the event one of them was to fail.
This article explores the concept of defence in depth, and how it applies to modern technology stacks and in the cloud.
💡 Digital Identity and Authentication

Time to go through the concepts of Digital Identity and Authentication, and how they are generally implemented in IT environments to automate access to websites, services and applications.
While this article does not require any specific technical knowledge, it is not a trivial topic, and I have purposely tried to not oversimplify some of the concepts. I have done my best to keep it easy to read, but feel free to send some feedback if some parts are too complex and you would like further clarifications.
💡 What is Identity Theft? (a beginner guide)

With Christmas coming fast, it is a great time to remember identity crime is a critical threat to the everyone. A short beginner guide on how to protect yourself against identity theft and what to do if your identity get stollen.
Read More…💡 Conference Transcript: Building an Information Security Policy Framework

Following my presentation on Building an Information Security Policy Framework at the "Implementing CPS 234" conference held in Sydney in May 2019, I received many requests to publish a transcript. Thank you all for your interest and for the large amount of feedback you shared with me. As promised, here is an augmented transcript of my presentation.
It covers an overview of what a Policy Framework is, and why it is an essential part of any Information Security program; the various existing frameworks used across the industry, their strengths and limitations; a methodology to create a flexible framework, supported by a risk assessment and a strong understanding of the assets owned by the institution and the threats they are exposed to; and an approach to define an adequate control set and how to prioritise its implementation.
💡 Creating a Secure Bring-Your-Own-Device Strategy

Corporate reality is that there is a growing interest from employees to use their personal devices for work. This can have a very positive impact on business – choosing which device is best for them and when, empowers workers and makes them more productive – but it also raises many security concerns for the enterprise – especially around access, confidentiality of information, compliance, security and privacy.
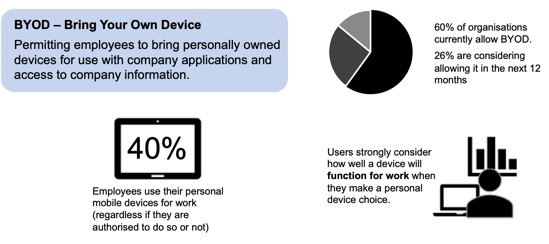
In order to define how employees will be able to interact with the corporate resources, the Bring-Your-Own-Device (BYOD) strategy is a critical part of your journey toward BYOD. It is there to define the capabilities your organisation offers to employees to use their personal laptops, smartphones or tablets for work.
To assist you in your journey, this article covers how to answer these questions and what are the options available for you in order to create a secure BYOD strategy.
💡 Public Cloud ☁️ - Australia and New Zealand Regulatory Landscapes

More than ever, financial institutions in Australia and New Zealand are moving toward public cloud computing as a way to benefit from easy to use, flexible, cost effective and reliable infrastructures and services. Despite its substantial benefits, cloud computing also creates a complex new environment for financial institutions to navigate. Regulators in Australia and New Zealand are evolving their requirements and guidelines. It results in a growing expectation that financial institutions have a robust governance over their outsourcing process and ensure a high level of oversight of their cloud service providers. This article discusses the regulatory requirements around usage of Cloud Services in Australia and New Zealand and how to satisfy them.
Read More…💡 APRA CPS 234: Are you ready?

The Australian Prudential Regulation Authority (APRA) just published the final version of the Prudential Standard CPS 234 (Information Security), that will be enforceable by 1 July 2019. Have you assessed your readiness? This article reviews the main expectations from the regulator and provides some guidance on how to ensure timely compliance.
💡 Security 101 – Why is it not safe to share sensitive information by email?

You are regularly being reminded by your security team that sharing sensitive information by email is not safe. But why? Well, good question. Here are some answers
Read More…💡 Understanding Meltdown and Spectre

As an executive or senior manager, what should I know and what should my company be doing about Meltdown and Spectre?
If you are not an IT Security specialist and you have been trying to understand what all the fuss is about - you are probably struggling to find articles that are not overly technical or too generic. Hopefully, this one will be answer your questions.
💡 The Robot, the Apple and the Coffee Bean

For a change, let’s talk about technologies…
Have you heard about Java? No? Well, even if you don’t know it, you are probably using Java everyday: On your computer, your mobile phone, your TV and more. Action(s) is made with Java, and it is the reason why you can run it indifferently on Windows, Linux or Mac OS X.
Apple made recently two big announcements regarding Java:
- The creation of a Mac App Store where Java applications will not be accepted
- The end of Apple’s support of Java on Mac OS X
The question that a lot of you have been asking us is: will these announcements impact the existence of Action(s) on the Mac OS platform?
The answer is No. We are still very committed to the Mac OS platform. We do not believe that Java will disappear from Mac OS X and we will continue to provide a high-quality – fully integrated version of Action(s) for Mac users.
Read More…