💡 Creating a Secure Bring-Your-Own-Device Strategy
Corporate reality is that there is a growing interest from employees to use their personal devices for work. This can have a very positive impact on business – choosing which device is best for them and when, empowers workers and makes them more productive – but it also raises many security concerns for the enterprise – especially around access, confidentiality of information, compliance, security and privacy.
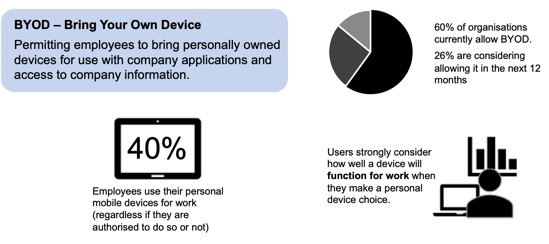
In order to define how employees will be able to interact with the corporate resources, the Bring-Your-Own-Device (BYOD) strategy is a critical part of your journey toward BYOD. It is there to define the capabilities your organisation offers to employees to use their personal laptops, smartphones or tablets for work. The BYOD strategy must address a number of questions:
- What are the expected benefits and risks associated to the solution?
- What type of governance should be in place? Especially, who owner what and who is authorised to do what.
- What services are going to be available to BYOD users?
- What are the responsibilities of each parties? Especially when it comes to supporting the solution
- What technology is going to be used to enable and control BYOD usage?
- What security is required and how will it apply to BYOD?
- What is the cost model of the solution?
What are the expected benefits and risks associated to the solution?
Studies shows that BYOD can create productivity gains by employees, increases employee morale and convenience by using their own devices and makes the company look like a flexible and attractive employer. More and more companies are using BYOD as a mean to attract new hires.Increased productivity comes from a user being more comfortable with their personal device; being an expert user makes navigating the device easier, increasing productivity. Additionally, personal devices are often more cutting edge as company technology refreshes don't happen as often.
Employee satisfaction, or job satisfaction, occurs with BYOD by allowing the user to use the device they have selected as their own rather than one selected by the IT team. It also allows them to carry one device as opposed to one for work and one for personal use.
Cost savings can occur on the company end because they now would not be responsible for furnishing the employee with a device, but keep in mind it is not a guarantee
Although the ability to allow staff to work at anytime from anywhere and on any device provides real business benefits; it also brings significant risks. It is imperative to put security measures in place lest information end up in the wrong hands.
BYOD can result in an increased security risk, especially when it comes to data breaches. For example, if an employee uses a smartphone to access the company network and then loses that phone, untrusted parties could retrieve any unsecured data on the phone. Another type of security breach occurs when an employee leaves the company, they do not have to give back the device, so company applications and other data may still be present on their device.
Furthermore, people sometimes sell their devices and might forget to wipe sensitive information before selling the device or handing it down to a family member. Various members of the family often share certain devices such as tablets; a child may play games on his or her parent's tablet and accidentally share sensitive content via email or through other online data storage solution such as Dropbox or Google Drive.
Employee privacy issues can also raise from the usage of BYOD. For example, monitoring of usage of personal devices must ensure that they only monitor work related activities or activities that accesses company data or information.
Additional technical consideration must be taken to ensure that the BYOD devices which connect to the network infrastructure to access sensitive information will be protected from malware. Traditionally if the device is owned by the company, IT would be able to dictate for what purposes the device may be used or what public sites may be accessed from the device. In a BYOD model, the company must expect users to use their own devices to connect to the Internet from private or public locations. The users could be susceptible from attacks originating from untethered browsing or could potentially access less secure or compromised sites that may contain harmful material and compromise the security of the device.
Software developers and device manufacturers constantly release security patches due to daily increase in the number of threats from malware. The IT department must be prepared to have the necessary systems and processes in place that will apply the patches to protect systems against the known vulnerabilities to the various devices that users may choose to use. It is a complex operational challenge, as it requires to quickly adopt the support necessary for new devices. Supporting a broad range of devices obviously carries a large administrative overhead. Usage of corporate devices have the benefit of selecting a small number of devices to support. While the BYOD policy could also limit the number of supported devices, this could defeat the objective of allowing users the freedom to completely choose their device of preference.
Another important issue with BYOD is of scalability and capability. Proper network infrastructure needs to be considered to handle the large traffic which will be generated when employees will start using different devices at the same time.
Finally, a key issue of BYOD which must not be overlooked is BYOD's phone number problem, which raises the question of the ownership of the phone number. The issue becomes apparent when customer-facing roles leave and take their phone number with them. Customers calling the number will then potentially be calling competitors which can lead to loss of business.
What type of governance should be in place?
Ownership
The first thing to consider is the ownership model: who will be owning (and as such, buying) the devise.Option A: Personally owned, company enabled (POCE) A personally owned device is any technology device that was purchased by an individual and was not issued by the company. A personal device includes any portable technology like camera, USB flash drives, mobile wireless devices, tablets, laptops or any personal desktop computer.
Option B: Corporate owned, personally enabled (COPE) As part of enterprise mobility, an alternative approach are corporate owned, personally enabled devices (COPE). With this policy purchases the devices to provide to their employees; the functionality of a private device is enabled to allow personal usage.
Management
The next step is to consider the device management model. That is, how the device will be managed, by who, and how it will be authorised to access the organisation data and systems.Option A: Mobile Device Management (MDM) MDM provides organizations with the ability to control applications and content on the device. It is a company managed device model and it consists in defining the appropriate security model for the device to access company information assets. It allows corporate applications to be installed directly on the device and also authorised direct connection between the device and the data repository and systems, acting similarly to a corporate own device.
It also usually allows advance action on the device if it becomes a security or individual concern, such as allowing remote management, remote deletion of data and remote deactivation.
Such approach required a higher level of support by the IT departments and required the definition of a set of minimum requirements for OS, security, application support and other criteria.
Such approach can also raise employee privacy and usability issues that lead to adoption resistance. Corporate liability issues could also emerge when if devices are wiped after employees leave the organization.
Option B: Virtualisation Virtualization is software technology that separates the desktop environment and associated application software from the physical client device that is used to access it.
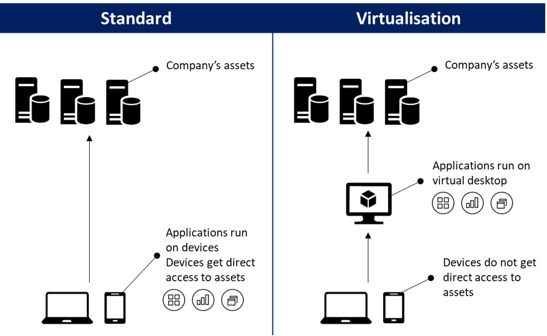
Virtualisation allows for a highly flexible and much more secure desktop delivery model. In addition, this approach supports a more complete desktop disaster recovery strategy as all components are essentially saved in the data centre and backed up through traditional redundant maintenance systems. If a user's device or hardware is lost, the restore is straightforward and simple, because the components will be present at login from another device. Because no data is saved to the user's device, if that device is lost, there is much less chance that any critical data can be retrieved and compromised.
Another advantage of virtualisation is that the desktop or applications virtualised run similarly on any compatible device. The size, operating system or browser of the devise does not impact the experience of the user, ensuring better compatibility.
One of the downside of virtualisation is that it requires a constant network connection to work. For applications relying on standard server / client model this is not an issue, but applications that offer offline options (such as Outlook or MS Office suite) will lose such capability. A solution to this limitation is to decide what applications are offered through virtualisation and consider offering “productivity” tools (for example MS Office) through standard install on the device.
Virtualisation also requires additional infrastructure to run and – if inappropriately setup and scale – could result in slowness that would create negative perception of the solution by the users.
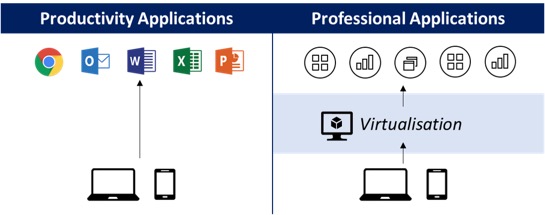
Option C: Hybrid To reduce the overhead of the MDM model and yet eliminate the limitations due to permanent connection requirement by virtualisation, a hybrid model can be considered. Such approach would result in a decision on an application basis to go through either virtualisation or standard install on the device. Usually, productivity tools would be offered on the device and professional applications for internal use would be offered via virtualisation.
Eligibility and registration
It is important to define the company eligibility approach to BYOD. Will the service be offered to all employees or will there be restriction based of their role, performance and/or frequency of travel.In most cases, the employee’s manager has authority to decide if the employee is a suitable candidate for BYOD, and final authorisation is subject to the approval of the Head of IT Security, or a duly appointed delegate.
While the strategy is being defined to allow any device to be used as part of BYOD without risk for the company, a registration process must in place to ensure all users understand their responsibilities when using BYOD capabilities.
The process can includes:
- Registration of the device with the IT department
- Signature of a consent form by the user, defining responsibilities and authority over the device and its data between the company and the user.
Controls
In addition to the safeguards defined above, regular 2nd level of controls should be considered to ensure the governance sound execution on an everyday basis:- BYOD Recertification: review of all users approved to use BYOD, and recertification by their manager that the authorisation stands.
- BYOD Reconciliation: review of all accesses by BYOD devices, and confirmation they have been approved via the BYOD approval process.
- Asset Management during termination: review of asset management (including BYOD) during termination process
What services are going to be available to BYOD users?
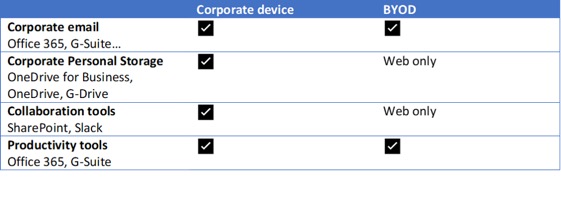
For each service and application available to the users, it is important to define if (and how) they will be offered to BYOD users.Publicly facing online services and applications are capabilities available directly from the Internet. These solutions allow access to authenticated users from any device and any location. They are generally Software as a Service (SaaS) solutions but can also be corporate solutions that have been designed with an outside facing interface.
Such solutions usually offer a web access, meaning that the user can access the service via a web interface which is not dependant on the device or browser. Some of them can also offer an app or a heavy client access that usually will offer additional capabilities, such as local download of data, offline access etc.
The table below is an example of publicly facing online services, and the type of access that can be offered to each of them. Capabilities marked as web only mean that, if technically possible, any app or heavy client capability will be deactivated for usage on BYOD.
Internal services and applications are available only from within the company network and are normally not exposed through direct Internet access.
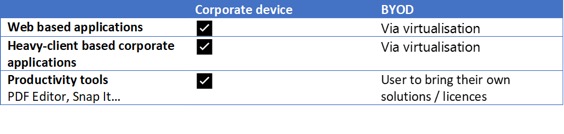
Such solutions include web-based applications (such as Intranet websites), and applications that execute from the user workstation (often legacy corporate applications, but also some productivity tools).
The table below is an example of internal services and applications, and the type of access that can be offered to each of them.
What technology is going to be used to enable and control BYOD usage?
Allowed Devices
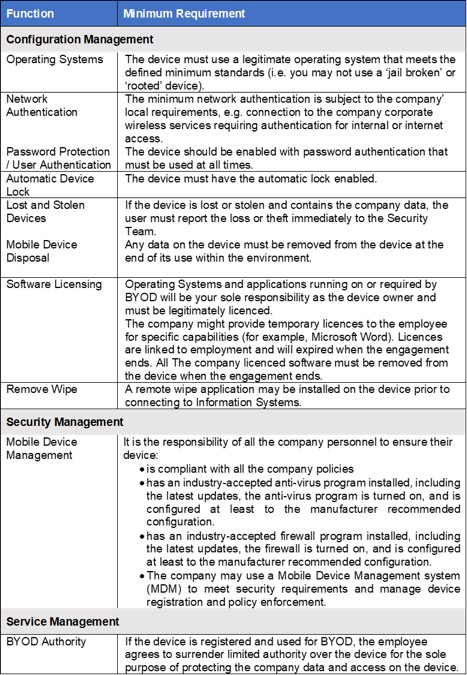
The strategy must define the minimum requirements for BYOD. BYOD applies to any portable technology like camera, USB flash drives, mobile wireless devices, tablets, laptops or any personal desktop computer.The burden of proof for meeting minimum requirements rests usually with the device owner.
Standard minimum requirements are presented in the table below.
Authentication
Authentication defines how employees are required to identify themselves when trying to access any type of asset or service. Authentication is a critical step when using a corporate device or within BYOD. Authentication processes can vary based on the actual location of the employee, especially if they are physically connected to the organisation network or if they are connecting from outside through the Internet or a VPN solution.
Network Access
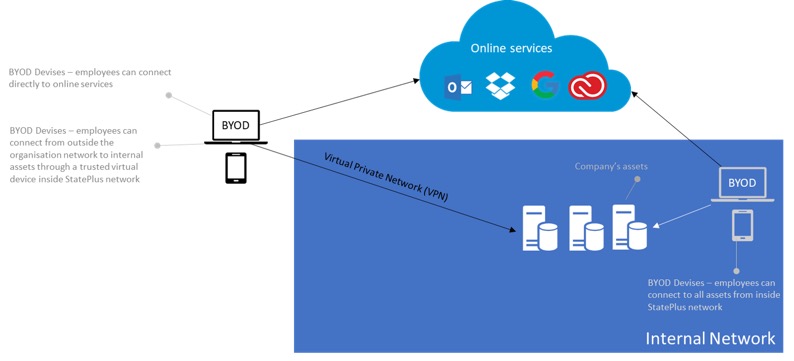
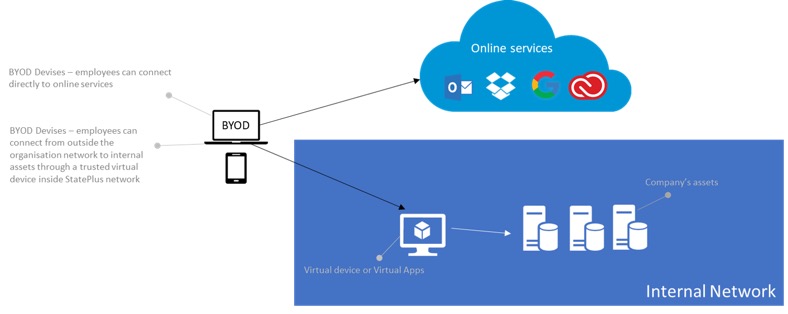
Corporate Network Access defines the capability for an employee to have direct access to assets and services that are located on the corporate network. That includes for example network shared folders (SMB) and intranet websites.Option A: Trusted Device (ideal for MDM Management Model)
Because the MDM management model allows greater control over the device, it can be considered as a trusted device and as such can be provided with direct access to asset (similar to a corporate device).
In such model, the device will be authorised to connect within the internal network and have direct access to resources within the network. If outside of the network, access will also be authorised (through a Virtual Private Network). Device will be also authorised to access online services, such as Office 365.
Option B: Untrusted Device (ideal for Virtualisation and Hybrid management models)
In the case of Virtualisation or Hybrid management model, the device is subject to lesser control from the company than a corporate device, and the virtualisation approach ensure an additional layer of security to limit the execution of critical applications within the confined space of a trusted environment.
BYOD devices should be considered as untrusted, and as such should not be allowed direct connection to the company network. Connection will be limited from the outside (via a public or a guest wifi for example).
The device will be allowed direct access to online services such as Office 365 but not direct access to the company resources. Virtualisation will be used to ensure secure access to the company internal assets.
Data Protection
By its inherent model, BYOD presents an increased risk around data loss and data breach. BYOD devices are subject to limited control by the organisation and are directly exposed externally. While virtualisation provides a good segregation to ensure the data from the company systems do not reach the device, online collaboration tools such as email and Office 365 offers capabilities allow to download and store the company data on the personal device, for example for advance editing or offline access, exposing them to data loss and data breach risk. However, such solutions also have capabilities to offer access to data online without any information being stored on the personal devices.Instead of reducing capabilities to the strict minimum when using a personal device, a Data Loss Prevention (DLP) solution can be considered to detect potential data breaches/data exfiltration transmissions and prevent them by monitoring, detecting and blocking data while in-use, in-motion, and at-rest.
The action taken by the DLP solution (record, alert and/or block the data transmission) is based on the data sensibility and defined in the DLP strategy. This allows users with their personal device to download and store low sensitive data on their device, but limit access to remote access when the data contains sensitive information. It also records and track all data access and transmission for investigation in case of incident.
Support
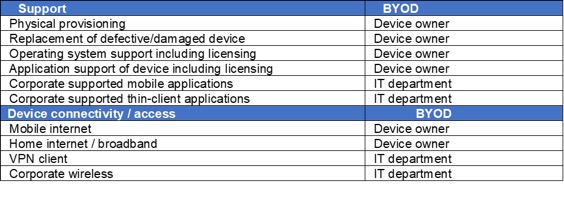
The IT team usually supports BYOD as far as ensuring the technology required on the company side is working as expected.While they can advise and occasionally assist, it is rarely the company mandate to ensure the user devise works properly or can access the company services. Employees are responsible for supporting their own device. The company will only provide support for the applications provided.
The table below is an example of support model for BYOD.
Depending on your internal rules, the company might or might not also be responsible for any costs incurred using the BYOD device. This will define if the company will reimburse or endure any voice or data charges, software or application acquisition fees, support or insurance costs associated with the device except in exceptional circumstances such as pre-approved excessive business requirements.
Personnel are responsible for abiding by all licence terms and conditions applicable to any software, apps, data or information provided by the company to their BYOD.
It is also a good idea to define the Service Level supported by the company when it comes to access through BYDO.
It is a good idea to support the BYOD strategy by a self-service capability, such as a BYOD portal - a central location for all staff to access information and tools. It can also be designed to be a “one stop shop” for employees to access web applications and licensed software.
The portal can be designed to:
- Provide access to BYOD policies and self-help documentation
- Provide a guide to register to the BYOD program
- Provide recommendations of best devices based on specific usages
- Reinforce rights and responsibilities that come with using a personally-owned device for business
- Reinforce acceptable use policies and segregate work data from personal data
- Display the most popular applications to facilitate quick access
- Offer a clean, simple layout and navigation.
- Be accessible from workstation and mobile devices
- Offer the IT department a simple capability to communication announcements and updates
What security is required and how will it apply to BYOD?
Specific security requirements and controls related to BYOD are to be defined to ensure data and services are protected. The sections below show possible clauses that can be included in your BYOD policy:Registration, ownership and rights
- Device must be registered before connecting to any Information Systems.
- Registration of any BYOD device should require completion of a service consent form with wet or electronic signature acknowledging receipt of a copy of this policy and any referenced documents and acceptance of all clauses of this and all related policies, standards, and guidelines. Consent forms will be retained by Human Resources.
- An upper limit can apply to the number of devices that can be registered.
- Devices used to access Information Systems must be for business use only and not accessible to other personnel nor to non-employees including, but not limited to, the personnel’s family.
- The company will retain the option to specify security configurations of the device to protect data and software stored on the device. These settings may include but are not limited to: Refusal to register a device that fails minimum requirements or that currently has installed banned software and services listed as determined by the Security Manager ▪️ Configuring certain security settings ▪️ Applying a login code with an acceptable level of complexity to enable secure access to the device ▪️ Automatically locking the device after an inactive timeout period (need to re-enter the login code) ▪️ Installing software and digital certificates necessary to maintain security ▪️ Encrypting data stored on the device;
- The company retains sole property of all data stored on the BYOD.
- The company has a right to inspect data held on their BYOD in accordance with The company policies.
- The company has the right to remotely wipe any device that has been registered or otherwise connected to the network facilities.
- The company has the right to inspect any configuration settings and log files on the device that are pertinent to maintaining the data security.
Device Usage
- Employees have sole responsibility for ensuring no other person has access to software or data stored on their device.
- Usually, the company will not monitor the web browser history on the device when not connected to the company network(s). Monitoring of web browser history when connected to the company network(s) may be conducted in accordance with applicable policies.
- The company may restrict access to internet websites, services or other elements for operational or policy reasons.
- The company may monitor the use of the BYOD. This information may be collected and archived.
- Employees are responsible for abiding by all licence terms and conditions applicable to any software, apps, data or information provided by Tte company to their BYOD.
- If the BYOD is lost or stolen, employees are responsible for reporting the event as soon as practicable to the Security Manager. Personnel must also: undertake a device wipe as soon as practicable via the installed remote wipe application; and take reasonable steps to ensure that it is replaced as quickly as possible
Protection of Data
- The company information, documents, and data classified as sensitive or above or that are subject to legal or professional privilege must not be stored on BYODs and/or unapproved cloud-based services.
- The company data must only be backed-up to approved locations either within the company Information Systems or approved cloud service locations or providers.
- Automated cloud backup should be disabled or the company data stored on the device should appropriately excluded from automated backups
- Employees should take reasonable steps to reduce the risk of losing their personal data. They may, for example, store their personal data separately from the company data through file partitions or using a separate memory card.
- Personnel are responsible for backing up and restoring the data and configuration settings of their BYOD. The company is not responsible for any personal loss or damage user may suffer by actions undertaken by the company to protect data stored on the device.
- If user suspect that their BYOD has been accessed, physically or by technical means, without authorisation, and it contains company data or configuration settings, this may be a Cyber Incident or Other Incident and must be immediately reported to The company security personnel.
De-registration
- The company, at its sole discretion, may deregister any BYOD at any time without warning.
- The company may deregister a BYOD that has not connected to the company Information Systems for more a specified period.
- If deregistered, all company data, applications and security controls will be removed from the device. The company reserves the right to audit the device to verify compliance with this clause.
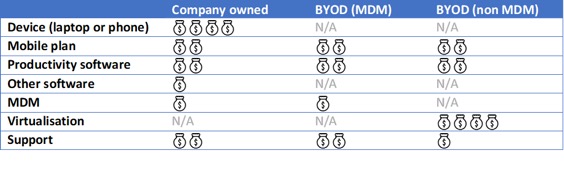
What is the cost model of the solution?
The BYOD Strategy is very often not designed to generate cost savings. While cost saving could result in the large adoption of the strategy it is not a guarantee and should not be pursue as such.The following tables present how the yearly BYOD cost for the organisation per year for a single user could be considered, and compare it to a company-owned device.